A report accompanied with a rating taxonomy aimed to help researchers and customers to determine appropriate payouts for bugs found by researchers in bug bounty programs has recently been released by Bugcrowd. These tools, especially the Vulnerability Rating Taxonomy (VRT), which details a number of vulnerabilities, classified by severity, are not only useful in the context of bug bounty programs – they could also prove useful in guiding organizations in prioritizing the discovery and remediation efforts of the vulnerabilities internally, prior to needing to make payouts to researchers, or worse, falling victim to an attack.
Both tools explore common vulnerabilities, and what those vulnerabilities would generally be worth, should a researcher discover them. The classification chart continues to reaffirm that vulnerabilities commonly detected by automated web security tools such as Remote Code Execution (RCE), SQL injection (SQLi) and XML External Entity Injection (XXE) are among the highest-weighted security bugs.
The ‘What’s a Bug Worth?’ report is more concerned with the actual worth of a vulnerability should it be discovered by a researcher. An interesting point that the report explores is that the value of a security bug is heavily based on what is referred to as the “security maturity” of an organization. Therefore, if an organization is already highly committed to good cybersecurity practices, bugs will be harder to find. The report even outlines a comparison of different mentalities, which can help gauge the maturity level of an organization when it comes to organization-wide security hygiene and outlook. This could prove to be useful when arguing the case for further cybersecurity spending, as often more senior company figures might not realize the security maturity that their company is lacking.

The next stage presented is the priority of the vulnerability, which is where the VRT chart comes into play. Vulnerabilities are assessed and then categorized between P1 (most severe) to P5 (least severe) which determines how much an organization should reward the researcher who reported it. Or, as organizations may prefer to use it, how much priority the various vulnerabilities should be given. Here the report gives a pared down version of their scale.
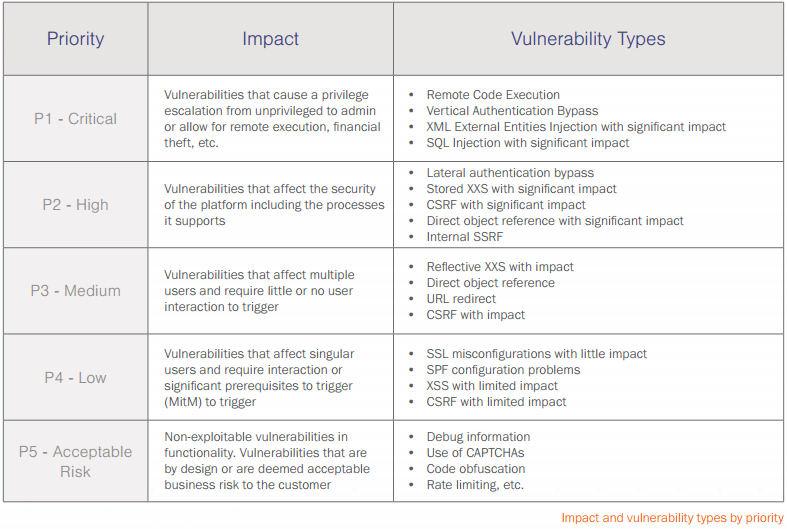
A number of the vulnerabilities covered could easily by picked up by an automated vulnerability scanner, therefore negating the need to establish a potentially expensive bug bounty program.
The report closes off by giving an indication of the cost running a bug bounty programme, which varies greatly depending on the first principle of security maturity.
For example, a P1 classified vulnerability payout is suggested to range between $1500 for an organization lacking a high-degree of security maturity, and $15,000 for more mature organizations. For the less severe P4 and P5 vulnerabilities the recommended payouts are significantly lower, ranging from $100 to $300.
This report is therefore helpful for organizations looking at incorporating bug bounty programs into their security programme to better understand what it would actually cost them.
While a bug bounty is an effective means of sourcing expertise outside of an organization to improve security, if used alone, without testing being done in-house, it could potentially become very expensive; especially when you consider that a large portion of vulnerabilities rated by Bugcrowd’s VRT are also vulnerabilities that automated vulnerability scanners like Acunetix are very good at finding. So perhaps it might be wise to consider automating your security testing first, and leveraging the power of the crowd to find vulnerabilities that can only be found manually by human penetration testers (such as vulnerabilities that require human logic and ‘hunches’ to uncover).
Get the latest content on web security
in your inbox each week.





