On the 12th of July 2011, Booz Allen Hamilton the largest U.S. military defence contractor admitted that they had just suffered a very serious security breach, at the hands of hacktivist group AntiSec.
Operation Anti-Security (AntiSec) is a hacking operation, carried out by two of the biggest names in the black-hat world – Anonymous, and LulzSec. They claim to target government corruption around the world. After hacking the servers of the Serious Organised Crime Agency in the UK, they turned their attention to the Arizona Department of Public Safety, releasing three separate caches of information.
The hacktivist group has also attacked the U.S. Department of Homeland Security, the Brazilian government, the Tunisian government, the government of Zimbabwe, and many others. Most recently, the Anonymous branch of Operation AntiSec breached the servers of NATO, stealing around a gigabyte of data. They claimed that the information was so sensitive that they are not going to release all of it, claiming that it would be “irresponsible”.
What Was Stolen
Dubbed “Military Meltdown Monday”, AntiSec claims to have stolen around 90,000 military email addresses, along with hashed passwords. These were saved into a highly compressed SQL dump, for easy downloading from The Pirate Bay (TPB).
The group, making the announcement using distinctly pirate-themed language, mentioned that they also found “maps and keys for various other treasure chests buried on the islands of government agencies, federal contractors and shady whitehat companies”.
The consulting agency has a policy of not commenting on leaks or attacks on its systems. However, a spokesman for the Department of Defence has indeed confirmed the attack, and has claimed that they are working together with Booz Allen Hamilton to investigate the extent and implications of this “disgraceful event”.
Booz Allen Hamilton tried their best to downplay the breach. In a press release after the attack they said, “At this time, we do not believe that the attack extended beyond data pertaining to a learning management system for a government agency.”
Jim Lewis, a cyber security expert with the Center for Strategic and International Affairs, echoed these thoughts when he said “I’m not sure it’s a big deal, they say they got lots of email addresses? Sounds like a scavenger hunt more than a hack.”
Booz Allen and Jim Lewis, I have some terrible news for you. This breach went beyond email addresses, this is not a scavenger hunt and the breach was not confined to your learning management system.
Read the next few sections of this article to understand the scope of the attack, gain insight into how it was performed and take a peek inside the stolen data.
How they did it
The hacking group did not tell us exactly how the hack was executed, however they did mention that their entry point was an SQL Injection attack. They managed to dump the entire database into a text file which means that they probably also gained root access to the systems. This theory is further enforced by the fact that they found and stole other files, including source code and some emails. This type of data is not normally siphoned off using SQL Injection but is the indication of a deeper penetration.
The security measures on the affected system did not impress AntiSec. Their description of the security goes like this, “…we found their vessel being a puny wooden barge. We infiltrated a server on their network that basically had no security measures in place”.
This statement is outright embarrassing for Booz Allen who claim that they offer “robust cyber security solutions”. They also state on their website that “cyber security cannot be treated as an afterthought.”
AntiSec enclosed an ‘invoice’ for the security audit:
“Enclosed is the invoice for our audit of your security systems, as well as the auditor’s conclusion.
4 hours of man power: $40.00
Network auditing: $35.00
Web-app auditing: $35.00
Network infiltration: $0.00
Password and SQL dumping: $200.00
Decryption of data: $0.00
Media and press: $0.00Total bill: $310.00”
Although they were probably just trying to be funny, some information can be elicited from this. First of all, it seems that the hack took four hours and was kicked off by a network audit, followed by an audit on the web applications. The web application audit is probably what caught the SQL Injection vulnerability in the first place. Network infiltration followed and an SQL dump was then taken. Prices in this invoice are an indication of how much effort was involved in each of the activities.
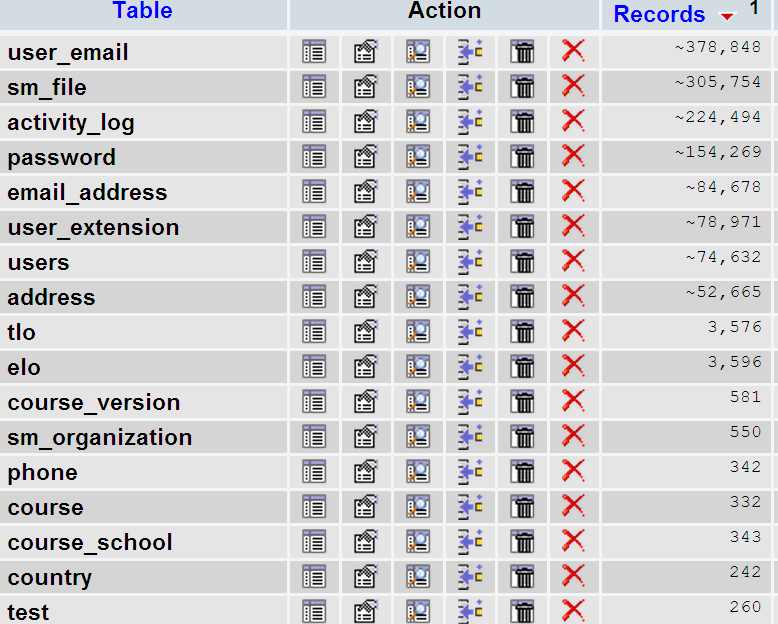
Data analysis
To understand the scope of the hack I decided to mount the SQL dump onto my database system and perform some analysis. The database is nearly a gigabyte in size and contains over 600 tables. Sifting through this database took time and patience, however I think I have uncovered a lot of juicy information that I would like to share with you.
So what are we dealing with here? The table login_text gives some context. It contains the message that is displayed when users log into the system. This text reveals the exact usage of this database. Here is an extract:
mysql> select TEXT from login_text;
“WELCOME TO THE JOINT KNOWLEDGE DEVELOPMENT AND DISTRIBUTION CAPABILITY (JKDDC) JOINT KNOWLEDGE ONLINE (JKO) PUBLIC PORTAL/LEARNING MANAGEMENT SYSTEM, A DEFENSE DEPARTMENT RESOURCE ADDRESSING INDIVIDUAL TRAINING NEEDS VIA DISTANCE LEARNING”
From this text we learn that we are dealing with the U.S Department of Defence distance learning programme. The login text continues:
“…the JKO portal provides access to Instant Messaging, Communities of Interest, and other Joint resources. To obtain a JKO portal account, please visit the JKO public site…”
With this we can see that the database is not only used as a Learning Management System, but also as a portal for other resources, an Instant Messaging service and also an Online Community.
The text also reveals two other public learning resources which are quite possibly also vulnerable to the same attack as this one. They are:
- https://jkolms.cmil.org/html/user/RedirectApplication.jsp
- http://www.usfk.mil/webtraining/
Another interesting note is this:
“U.S. Department of Defense Students – Please ensure you include your Social Security Number (SSN) when registering for an account with the JKO LMS…”
This statement leads me to the next stage of the investigation – what personal user information can be gathered from this stolen database?
The tables that will answer this question are: user, user_extension, address, phone and user_email.
A few SQL queries will reveal all.
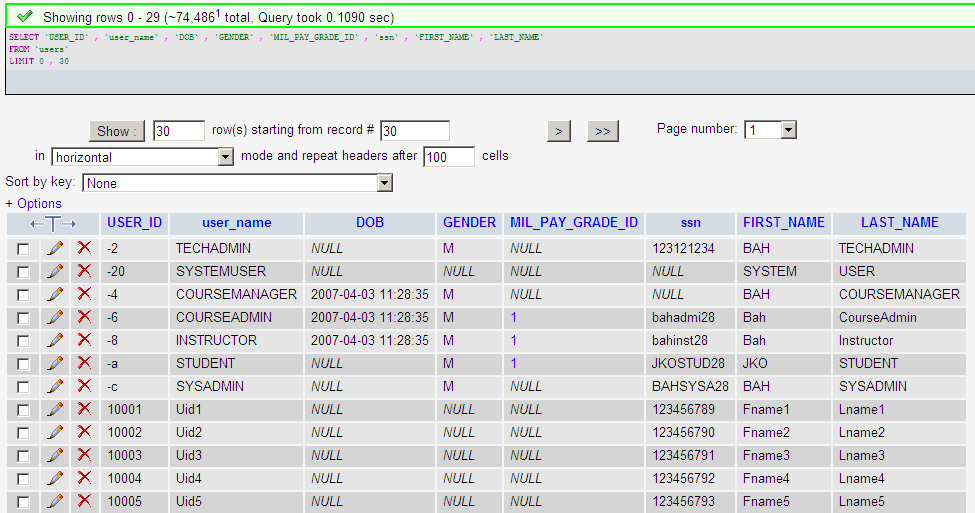
The user table is my starting point.
The users table contains a lot of information including the date of birth, gender and social security number. After browsing the data I can see that most of the social security numbers are invalid and the user first and last names are not used. We can also see some system users such as SYSADMIN. These users have a strange social security number that sort of looks like a passsword, however I cannot tell for sure.
There are over 74,000 users in this table. Most of the entries were created in August 2010, however some records indicate that this database dates back to early 2008. One record was modified in March 2011 meaning that this database was being used until recently.
So, where are these users from? The address table should give us that information.
The address table is ripe with information. It gives full addresses for every user on the system. Interesting to note how many countries there are. I counted 89 distinct countries using the following SQL command:
SELECT distinct `COUNTRY_CD` FROM `address` order by country_cd asc
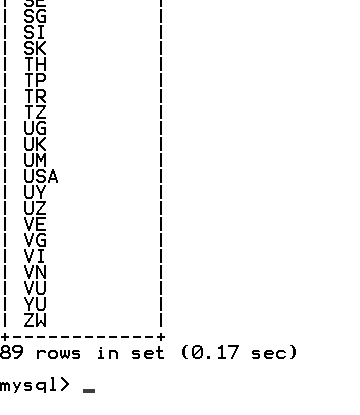 The phone table seems to have valid phone numbers linked to the user ID. It however only contains only 350 records, most of which date back to 2007, so they are probably old records from a previous version of the database.
The phone table seems to have valid phone numbers linked to the user ID. It however only contains only 350 records, most of which date back to 2007, so they are probably old records from a previous version of the database.
The user_extension table contains a promising 70,500 records, however it also fails to reveal anything interesting apart from email addresses lost in a sea of NULLs.
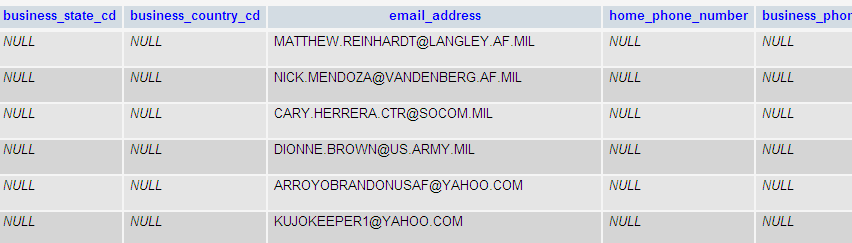
Another interesting table is the one called email_address. The table contains 84,000 records, however some of them are listed as “NOEMAIL@JFCOM.MIL”. When this email address is filered out I am left with 69,000 unique email addresses. These can be linked to the mailing addresses making them a very nice data set for spammers, scammers and phishers.
Here is my output:
SELECT USER_ID, EMAIL_ADDRESS, CREATED_DATE FROM `email_address` Where email_address <> ‘NOEMAIL@JFCOM.MIL’ GROUP BY EMAIL_ADDRESS ORDER BY CREATED_DATE DESC
Most of this data comes from military sites, however there are a few personal or company email addresses too. Interestingly the full name of the person is peresent in his email address. The bar chart below shows how the majority of email addresses are distributed over top-level domains.
 So far I have data mined personal information for more than seventy thousand military personell, however the group AntiSec mentioned a ‘treasure trove’ of information that will enable them to penetrate further into other miliary networks. I scavenged the database for these nuggets, here is what I found.
So far I have data mined personal information for more than seventy thousand military personell, however the group AntiSec mentioned a ‘treasure trove’ of information that will enable them to penetrate further into other miliary networks. I scavenged the database for these nuggets, here is what I found.
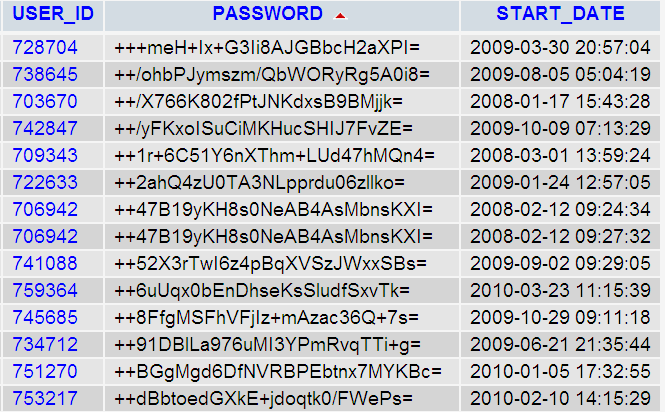
The password table contains 155,000 records containg the password of all the users in the database. Many users use the same passwords on multiple sites, so this information could be a very big asset for potential attacks on the users and their organizations. You can see a screen shot of the passwords here:
The password is reportedly in this format: base64(sha1(password)). If this is really the case, then all passwords could be revealed by brute-force. This can take some time for the strongest passwords, however Anonymous have already solicited the help of the public by providing the files for download in an easy format, and giving a link to the associated email addresses. Furthermore, I also noticed many duplicate passwords, this is an indication that password salting is not taking place. Salting is a technique used to slow down brute-force attacks on hashes.
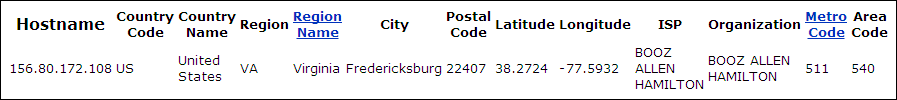
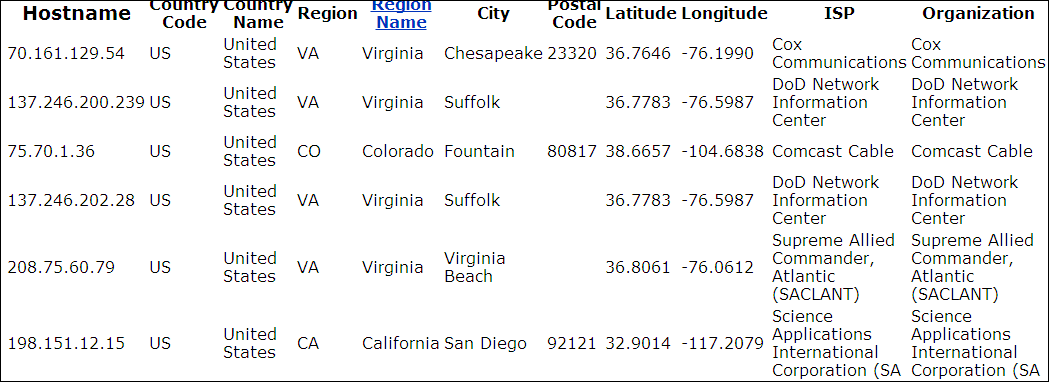
One very interesting table is the activity_log. This table logs activity of online users and contains informartion such as the IP address of the user and his user-agent, which reveals the operating system and web browser that he is using. This information makes targeted attacks much more probable.
As you can see, some of these IP addresses are internal addresses, some logins also appear to be from the local machine. Logins are as recent as April 2011, meaning that the password list is very ‘fresh’. The browser and operating system are also valuable information to a hacker. It’s disheartenining to see so many Internet Explorer browsers in use.
Some other public IP addresses are also owned by Booz Allen themselves:
In all, I counted over 47,000 unique IP addresses using the following SQL command:
SELECT COUNT( DISTINCT ip_address ) FROM `activity_log`
Other IP addresses are coming from all over the place. I picked a handful and found them to come from diffrerent DoD agencies distributed across America.
Apart from personell information, I was also able to find other data in some miscellaneous tables. This data can all be used for further hacking into the government’s networks.
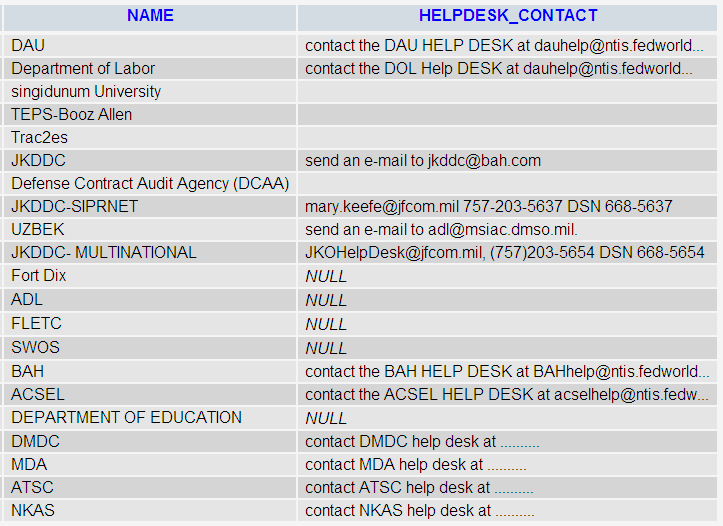
The table application_owner lists the possible next targets from AntiSec, as these are all contributors to the LMS.
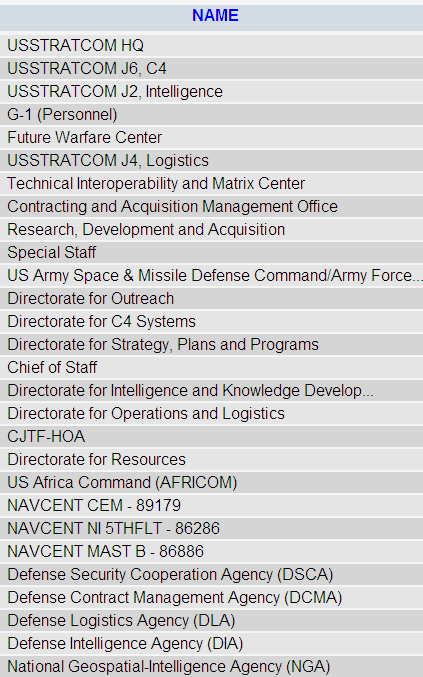
Some more organizations can be gleaned from the table mil_quota_source_node. A total of 134 different agencies can be identified from this table.
Finally, I look at the system user table where I find a few more juicy bits. Hosts, usernames and hashed passwords which appear to be unsalted (notice same hash is listed twice.)
Verdict
I set out on this investigation to determine whether AntiSec was just bluffing, and whether Booz Allen were right to downplay the incident. My initial hunch was that a bunch of teenagers were making the headlines again because of some silly data that they managed to scrape off some ageing website. I could have not been more far off from the truth.
It is evident that this is no small breach. The sheer numbers of usernames, passwords and email addresses, along with hostnames, IP addresses, user-agents and internal user names makes this hack look like the beginning of a larger wave of attacks that will hit the American government in the coming months.
Closing
To conclude I would like to directly quote the motto of Anonymous. Their motto never scared me, however as I look deeper into the work of this group I start feeling more and more uneasy. Should we be taking these anarchists more seriously?
“We are Anonymous.
We are Legion.
We are Antisec.
We do not forgive.
We do not forget.
Expect us.”
Get the latest content on web security
in your inbox each week.