WP Live Chat for WordPress is a very popular plugin used by many companies to provide online support. Currently, it has more than 50000 active installations. Very recently, researchers from Alert Logic found an authentication bypass vulnerability in this plugin. This vulnerability may be used by an attacker to exfiltrate chat logs and manipulate chat sessions.
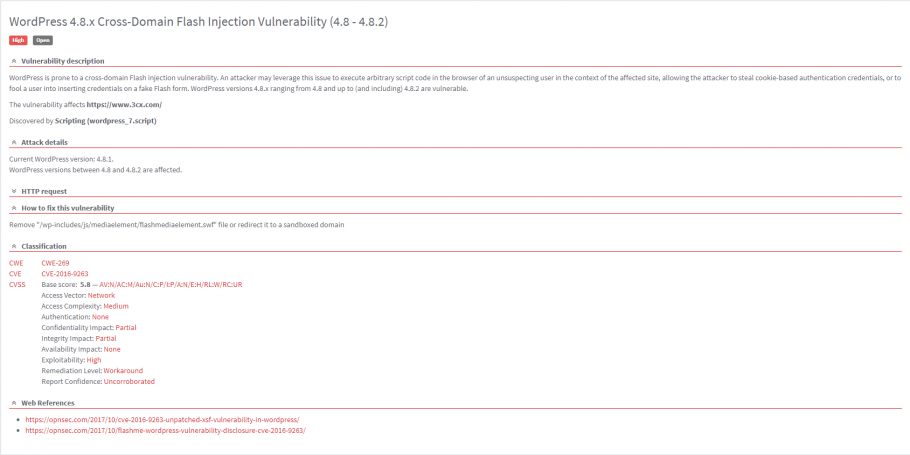
Anatomy of the Vulnerability
The vulnerability is caused by a mistake in the logic of a key function that checks for permissions. This function is defined in the modules/api/wplc-api-functions.php file:
function wplc_api_permission_check(){
return is_user_logged_in() ? check_ajax_referer( 'wp_rest', '_wpnonce', false ) : true;
}
The function wplc_api_permission_check() uses two WordPress functions to check if the user is authenticated and if the user has authorization: is_user_logged_in() and check_ajax_referer(). Due to the developer’s mistake, if is_user_logged_in() returns false, the wplc_api_permission_check() function returns true and check_ajax_referer() is not executed at all.
The wplc_api_permission_check() function is used in the definition of three key REST API endpoints (in the modules/api/wplc-api-routes.php file):
register_rest_route('wp_live_chat_support/v1','/accept_chat', array(
'methods' => 'GET, POST',
'callback' => 'wplc_api_accept_chat',
'permission_callback' => 'wplc_api_permission_check'
));
register_rest_route('wp_live_chat_support/v1','/end_chat', array(
'methods' => 'GET, POST',
'callback' => 'wplc_api_end_chat',
'permission_callback' => 'wplc_api_permission_check'
));
register_rest_route('wp_live_chat_support/v1','/send_message', array(
'methods' => 'GET, POST',
'callback' => 'wplc_api_send_message',
'permission_callback' => 'wplc_api_permission_check'
));
As defined using these three calls, endpoint access depends on the result of the wplc_api_permission_check() function. Therefore, if the user is not authenticated, access is granted, which should definitely not be the case.
This vulnerability was reported by Jonny Milliken of Alert Logic and classified as CVE-2019-12498.
How to Remediate
The wplc_api_permission_check() function was fixed in the latest release of WP Live Chat:
function wplc_api_permission_check(){
return check_ajax_referer( 'wp_rest', '_wpnonce', false );
}
Therefore, all you need to do is update your plugin to version 8.0.34 or later if available. The upcoming release of Acunetix will also test for this vulnerability.
WP Live Chat seems to have a bad streak. This is the third vulnerability discovered in this plugin in the last couple of weeks. Others include an arbitrary file upload vulnerability and a stored XSS. If you use WP Live Chat, keep your hand on the pulse and make sure that you always update it as soon as possible.
Get the latest content on web security
in your inbox each week.