One of the most important benefits of using Acunetix is the fact that you can integrate it into your SDLC so that you can scan your applications automatically and as early as possible. The earlier you scan and the earlier you eliminate vulnerabilities, the less time and resources you waste. This is the principle behind the DevSecOps approach that has been gaining popularity around the world.
Jenkins is the most popular CI/CD tool in the world used in most DevOps environments. You can download Jenkins from https://jenkins.io/download/. Jenkins works on platforms such as Windows, Linux distributions, and in Docker containers. You can fully integrate Acunetix with Jenkins so that your builds include a web security scan.
Step 1. Install the Acunetix Plugin for Jenkins
- In the Jenkins UI, click on the Manage Jenkins menu option.
- On the Manage Jenkins page, click on the Manage Plugins option. This will open the Jenkins Plugin Manager page.
- On the Jenkins Plugin Manager page, click on the Available tab.
- In the Filter field, type Acunetix.

- Click on the checkbox next to the Acunetix plugin.
- Click on the Install without restart button.
- When the installation is complete, click on the checkbox next to Restart Jenkins when installation is complete and no jobs are running.
Step 2. Find the Certificate Store Path
You need the certificate store path to install the Acunetix SSL certificate into the Jenkins CA store.
The default certificate store path is JAVA_HOME_FOLDER\lib\security\cacerts. You need to identify the JAVA_HOME_FOLDER for the Java binary running your Jenkins service. Keep in mind that your machine may have several installations of different versions of Java.
Jenkins on Windows
To find out which Java installation runs the Jenkins service, open the jenkins.xml file in the Jenkins installation directory and look for the executable tag. For example:
<executable>%BASE%\jre\bin\java</executable>
The %BASE% variable refers to the Jenkins installation directory. In the case of Jenkins 2.222.4 (32-bit), this is C:\Program Files (x86)\Jenkins. Therefore, the Java executable is C:\Program Files (x86)\Jenkins\jre\bin\java.
To find the java.home directory for the Java instance running the Jenkins service, run the following command:
"C:\Program Files (x86)\Jenkins\jre\bin\java" -XshowSettings:properties -version 2>&1 | find "java.home"
The output will show you the relevant java.home directory:
java.home = C:\Program Files (x86)\Jenkins\jre
Since the certificate store file is JAVA_HOME_FOLDER\lib\security\cacerts, we now know that in this example we need to use the certificate store file C:\Program Files (x86)\Jenkins\jre\lib\security\cacerts.
Jenkins on Linux
You first need to know which Java binary is running your Jenkins service. From the command line, run the following:
ps -aux | grep jenkins
You should receive output showing all processes that include jenkins in the name or path, for example:
jenkins 11044 0.0 0.4 21156 9060 ? Ss 13:42 0:00 /lib/systemd/systemd --user
jenkins 11045 0.0 0.1 106264 2620 ? S 13:42 0:00 (sd-pam)
jenkins 11058 0.0 0.0 5712 160 ? S 13:42 0:00 /usr/bin/daemon --name=jenkins --inherit --env=JENKINS_HOME=/var/lib/jenkins --output=/var/log/jenkins/jenkins.log --pidfile=/var/run/jenkins/jenkins.pid -- /bin/java -Djava.awt.headless=true -jar /usr/share/jenkins/jenkins.war --webroot=/var/cache/jenkins/war --httpPort=8080
jenkins 11059 3.1 14.0 2623256 287656 ? Sl 13:42 0:22 /bin/java -Djava.awt.headless=true -jar /usr/share/jenkins/jenkins.war --webroot=/var/cache/jenkins/war --httpPort=8080
root 11194 0.0 0.0 6048 888 pts/0 S+ 13:54 0:00 grep jenkins
In this case, we can see that the java executable is /bin/java (your system may have different configuration) but it’s almost certainly a symlink to the real binary installed by the JDK or JRE package or even possibly a chain of symlinks.
To find the java.home directory for the Java instance running the Jenkins service, run the following command:
/bin/java -XshowSettings:properties -version 2>&1 | grep "java.home"
Replace /bin/java with the executable found earlier. The output will show you the relevant java.home directory:
java.home = /usr/lib/jvm/java-11-openjdk-amd64
Since the certificate store file is JAVA_HOME_FOLDER/lib/security/cacerts, we now know that in this example we need to use the certificate store file /usr/lib/jvm/java-11-openjdk-amd64/lib/security/cacerts.
Step 3. Install the Certificate into Your Java Keystore
Jenkins on Windows
Run the following command from the command prompt:
keytool -import -trustcacerts -alias AcunetixCA -keystore "C:\Program Files (x86)\Jenkins\jre\lib\security\cacerts" -file C:\ProgramData\Acunetix\certs\ca.cer
Confirm that you have successfully installed the certificate on Windows:
keytool -list -keystore "C:\Program Files\Java\jre1.8.0_251\lib\security\cacerts" -alias AcunetixCA
Jenkins on Linux
Run the following command from the command prompt:
keytool -import -trustcacerts -alias AcunetixCA -keystore /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.252.b09-2.el8_1.x86_64/jre/lib/security/cacerts -file /home/acunetix/.acunetix/data/certs/ca.cer
Confirm that you have successfully installed the certificate on Linux:
keytool -list -keystore /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.252.b09-2.el8_1.x86_64/jre/lib/security/cacerts -alias AcunetixCA
The Result on Windows and Linux
If the certificate was successfully installed, you will see the AcunetixCA details, for example:
Enter keystore password:
AcunetixCA, 15 May 2020, trustedCertEntry,
Certificate fingerprint (SHA-256): E6:01:86:F3:43:33:97:25:71:B9:4E:BC:D9:08:30:AC:18:75:F6:9A:E6:D0:09:1D:D0:90:DF:2A:1D:8E:97:BA
Step 4. Configure the Integration between Jenkins and Acunetix
- In the Jenkins UI, click on the Manage Jenkins menu option.
- On the Manage Jenkins page, click on the Configure System option. Scroll down to the bottom, to the Acunetix section.

- Ensure that the Acunetix API URL value is correct. By default, the Acunetix API URL field is based on localhost.
- The Acunetix CA certificate is issued for the hostname that you selected when you installed Acunetix. In Jenkins, you have to use the same hostname.
- If your Jenkins runs on a different host than Acunetix, you need to make Acunetix reachable from hosts other than localhost.
- If you are using Acunetix Online, use https://online.acunetix.com/api/v1.
- Click on the Add button next to the Acunetix API Key field and select the Jenkins option.

- In the Jenkins Credentials Provider dialog:
- In the Kind field, select Secret text.
- In the Scope field, select Global (Jenkins, nodes, items, all child items, etc).
- Open the Acunetix user interface to retrieve the Acunetix API key:
- Go to your Profile page (you must be the administrator), and scroll to the bottom.
- If you don’t have an API key yet, click on the Generate New API Key button.
- Click on the Copy button to copy the API key to the clipboard.
- Go back to the Jenkins UI.
- In the Secret field, paste the Acunetix API key.
- Click on the Add button to close the Jenkins Credentials Provider dialog.
- Click on the Apply button to save the Acunetix API key settings.
- Click on the Test Connection button – you will see the message Connected Successfully.
Connection Issues – Notes and Troubleshooting
The Acunetix CA certificate is issued for the hostname that you selected when you installed Acunetix. In Jenkins, you have to use the same hostname. If you want to use the IP address, you need to generate the Acunetix CA certificate again for the IP address.
If you use a hostname instead of an IP address or the other way around, Jenkins will respond with a Connection refused error. To further investigate the encountered issue, follow these instructions for your OS.
- Windows: By default, you can find Jenkins logs in %JENKINS_HOME%\jenkins.out and %JENKINS_HOME%\jenkins.err, unless customized in %JENKINS_HOME%\jenkins.xml.
- Linux: By default, you can find Jenkins logs in /var/log/jenkins/jenkins.log, unless customized in /etc/default/jenkins (for *.deb) or via /etc/sysconfig/jenkins (for *.rpm).
Step 5. Add an Acunetix Scan as a Build Step in a Jenkins Job
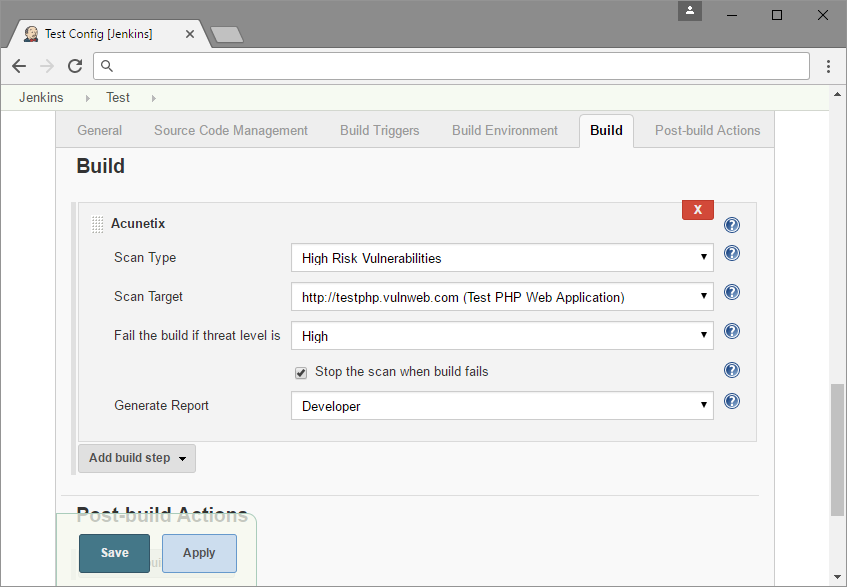
To add an Acunetix scan as a build step in a Jenkins job, navigate to the configuration of an existing job or create a new job. In the Build step, select Acunetix from the Add build step drop-down.

You will see the following options:
- Scan Type: Choose a scan type for the scan. Scan types are used to reduce the scope of tests that the scanner runs during the scan.
- Scan Target: Choose a scan target that you wish to scan. Scan targets are obtained from Acunetix with the exception of targets that require manual intervention.
- Fail build if threat level is: Choose at which scan threat level to fail the Jenkins build (High, Medium, or Low).
- Stop the scan when build fails: Select this checkbox if you would like to abort the scan when the fail condition in Fail build if threat level is is met.
- Generate Report: Choose a report to generate upon completion of the scan. A download link will be provided in the job console output. You can also later access this report in Acunetix.
Get the latest content on web security
in your inbox each week.