Interactive Application Security Testing (IAST) with AcuSensor
The AcuSensor technology is an additional component of Acunetix. When you install and use AcuSensor, Acunetix becomes an IAST solution (grey-box scanner), not just a DAST scanner (black-box scanner). AcuSensor works with applications written in Node.js, PHP, Java (including the Spring framework), and ASP.NET.
Scan every file — even hidden ones
Most scans miss unlinked and hidden files because crawlers can’t see them. By deploying the IAST sensor within your runtime environment, you’ll gain enhanced visibility into the backend of your web application — this encompasses information about the files utilized by the web application as well as the routing within it. When web API routing is present, you can now discover APIs that are used by the web application.
With Acunetix, you can also import API definition files and links so you can perform tests on all your APIs that use a REST, SOAP, or GraphQL architecture.
Now, you can have confidence that every part of every page has been mapped and tested, which ultimately means bad actors have fewer ways to attack you.
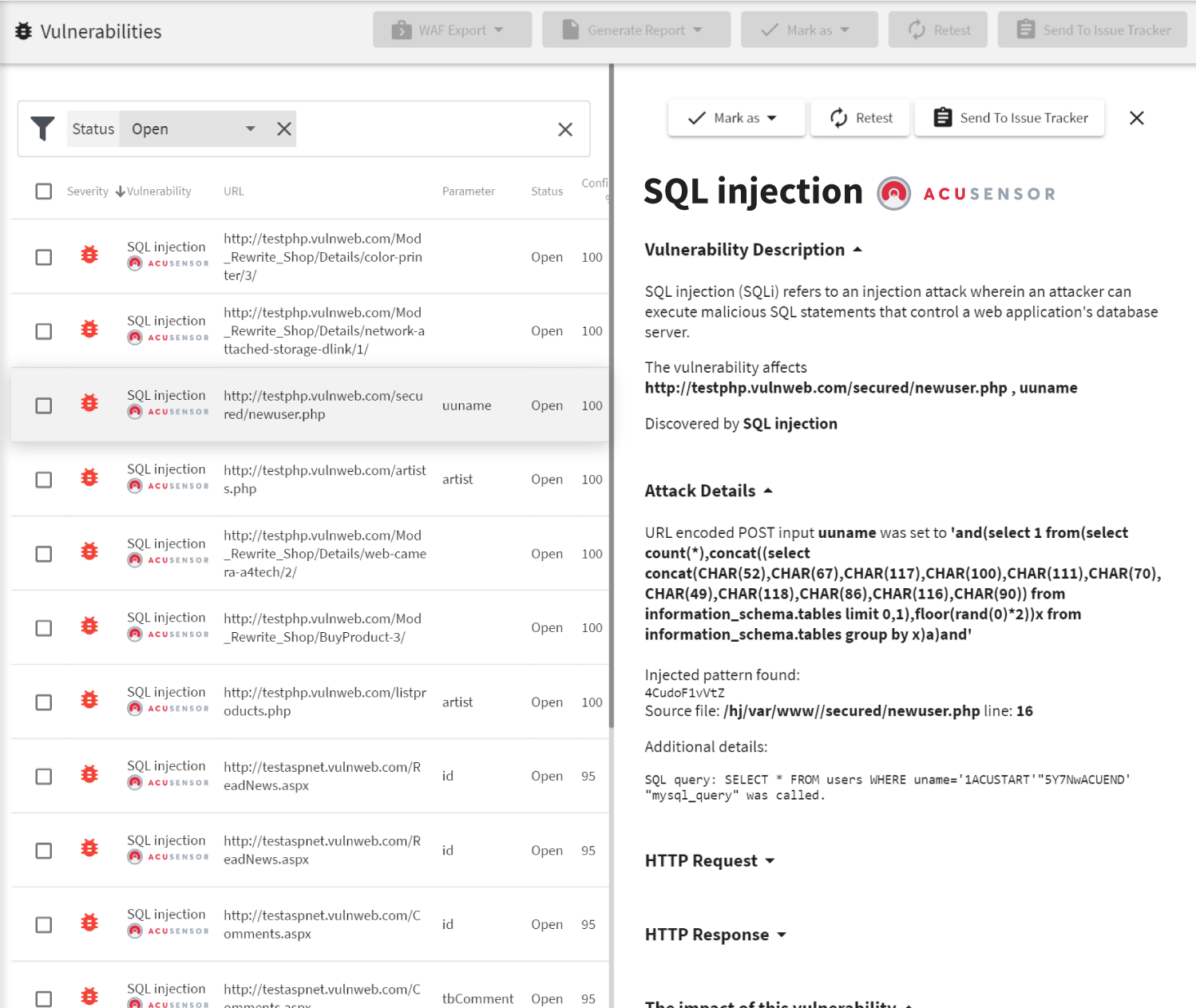
What Are the Benefits of AcuSensor?
When you use AcuSensor, Acunetix gets additional information from the server back end, at the time when Acunetix is scanning the web application. This additional information introduces a number of improvements.
- Ease of remediation: AcuSensor connects to the code interpreter or compiler (depending on the language) and it can identify the exact line of source code (for PHP) or point to a location in a stack trace (for Java and ASP.NET). With this information, your developers can fix vulnerabilities much faster.
- Greater precision: AcuSensor can detect the following vulnerability types with 100% confidence: SQL Injection, code injection, CRLF injection, directory traversal, arbitrary file creation/deletion, email header injection, file upload, file inclusion, file tampering, PHP code injection, and PHP SuperGlobals overwrite.
- Full coverage: AcuSensor provides a full directory listing of the web application, ensuring that the entire web application is scanned, including any hidden, unlinked locations. Additionally, AcuSensor can discover hidden GET and POST inputs, even if these are not used within the web application.

How Does AcuSensor Work?
The Acunetix scanner works by sending payloads and analyzing responses. When the web server receives the payload, it executes back-end code. If AcuSensor is installed, it analyzes the executed back-end code and provides the scanner with additional information.
- You must install AcuSensor on the server for the selected language. AcuSensor is available for Linux/UNIX and Windows servers.
- AcuSensor works directly with the PHP interpreter as well as Java and ASP.NET bytecode compilers.
- You do not need to modify your source code at all to use AcuSensor. This is a major advantage over IAST offerings that require you to compile sensors within your code, often requiring you to change your build process or add software dependencies to your project.

When to Use IAST?
AcuSensor works best in specific environments and is not recommended for some of the others. To get the best out of AcuSensor, use it in the right environment.
- You should install AcuSensor on your staging servers. This is the best place to perform IAST analysis.
- You may install AcuSensor on virtual machines to perform IAST analysis as part of CI/CD pipelines. In this case, the AcuSensor installation would need to be done as part of the CI/CD pipeline.
- We do not recommend installing AcuSensor on production servers. An active AcuSensor consumes some resources, so your production web applications may run slower.
- AcuSensor is currently available for Node.js, PHP, ASP.NET, and Java. Let us know if you would like us to create an AcuSensor for your technology.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox