Detecting Intrusions vs. Preventing Them
In an ideal scenario, your web application would be impermeable to intruders. Unfortunately, new vulnerabilities in web applications are being discovered all the time and sometimes we might not be aware that an intrusion has taken place until after it has occurred. Although the first case is more serious than the second (prevention is always better than cure), a sound security infrastructure requires more than simply installing tried and tested policies and solutions. Intrusion detection systems that monitor for malicious activity and suspicious web traffic can help to identify when an intrusion has taken place. LEARN MORE: Web Vulnerability Scanner by AcunetixActive Intrusion Prevention with Acunetix
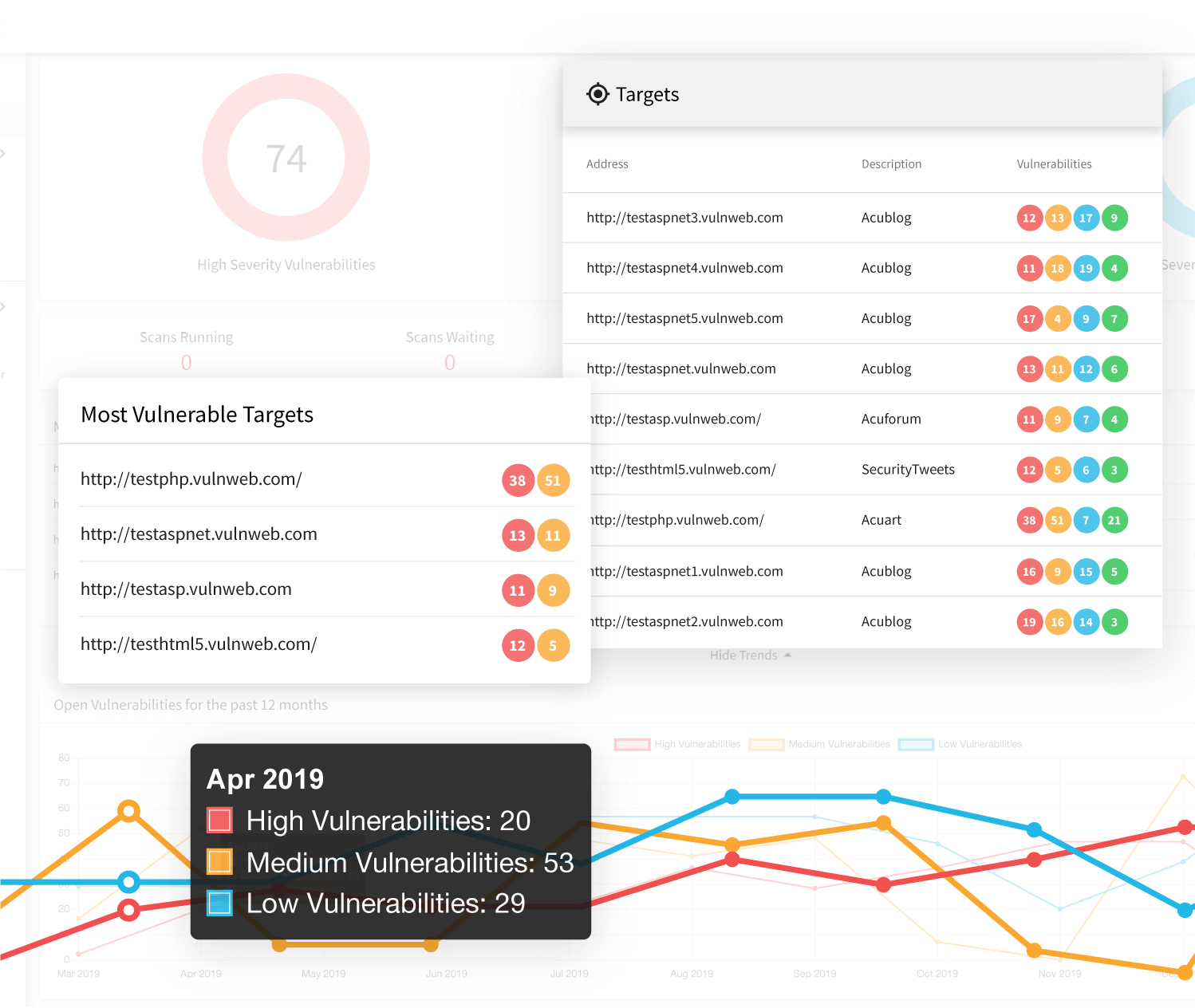
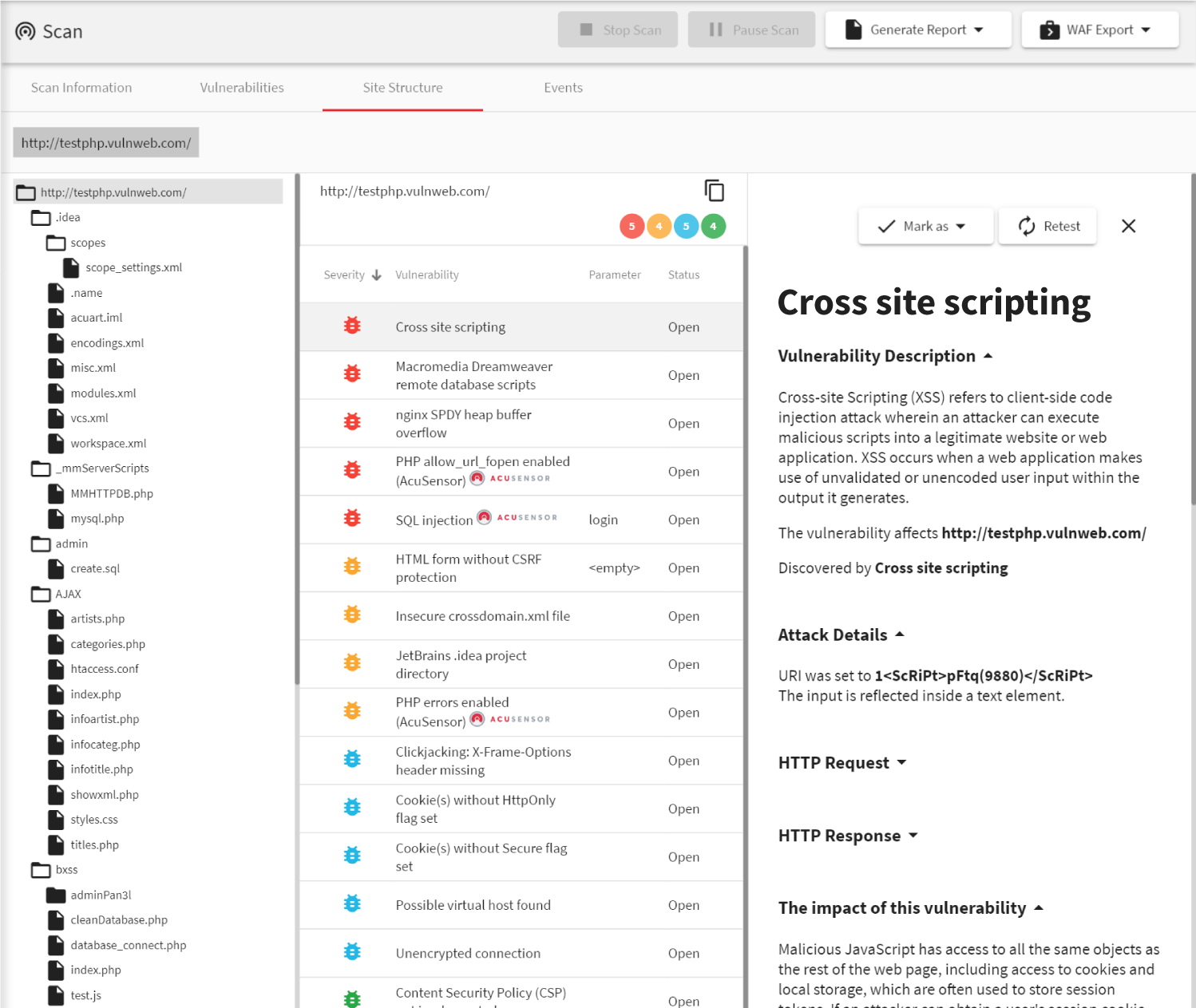
However, Intrusion detection, although paramount, is a passive form of security. Therefore, you need a set of tools that allow you to see whether people can penetrate these security measures. Acunetix vulnerability scanner is one such tool. The web application layer is significantly different from the network layer simply because web applications (e.g., shopping carts, login forms, contact us forms) need to have direct access to your database.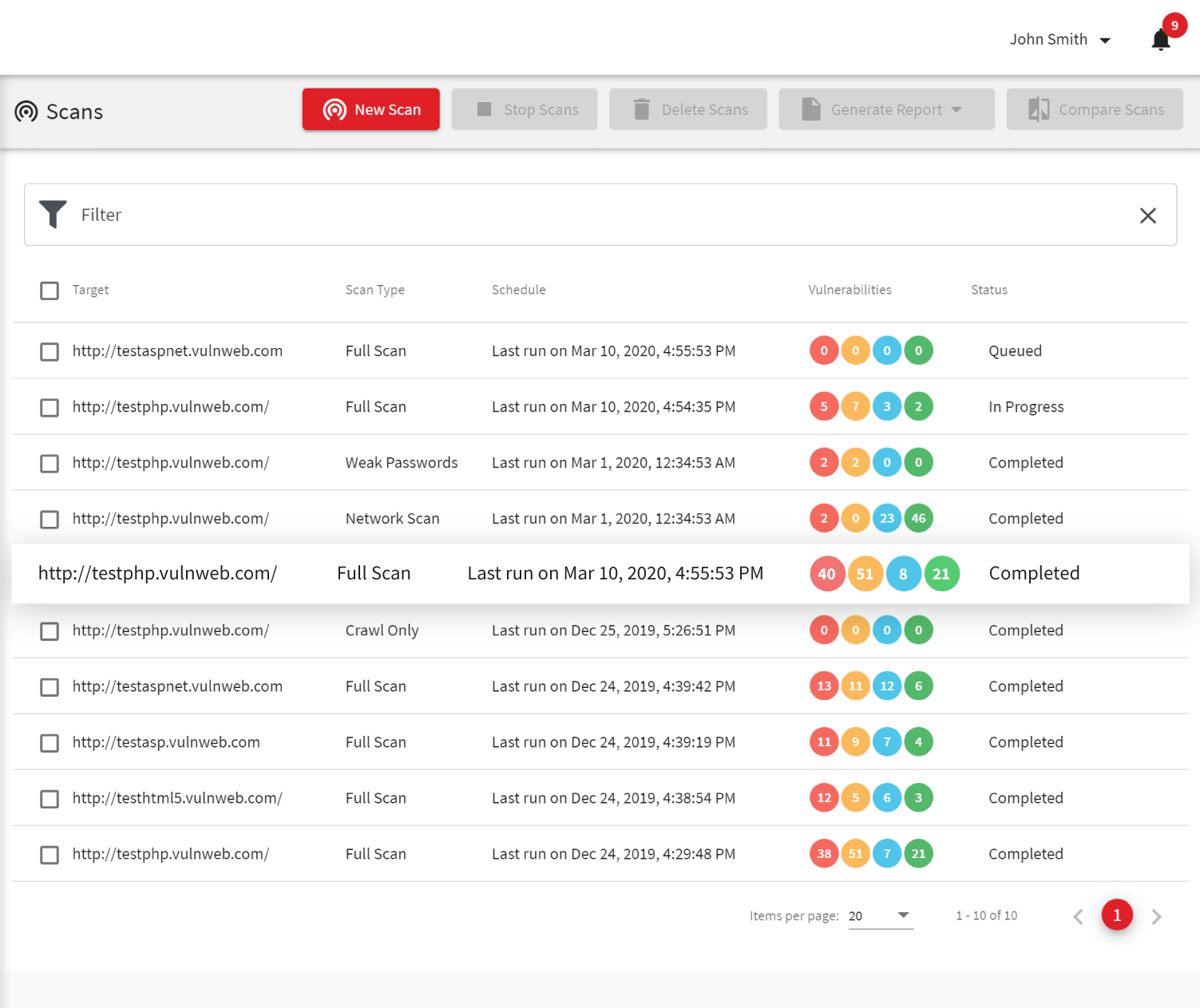
Web Applications Need Active Protection
Since your website needs to be public, all your security and intrusion detection mechanisms will allow public web traffic to communicate with your web application/s (generally over port 80/443). The web application has open access to the database in order to return (update) the requested (changed) information. This means that at any point in time someone with significant knowledge of databases and coding can manipulate any single application on your website to yield (delete or change) data contained in the database. In these cases, intrusion detection systems might alert you to the activity or to some suspicious traffic but the damage will already have been done. The only way to ensure that this doesn’t happen is to scan your web applications regularly using a web vulnerability scanner such as Acunetix. The solution will tell you which web applications are weak and therefore can be manipulated. Acunetix will report the type of vulnerabilities and give you recommendations how to best proceed in fixing these weaknesses that will be used by hackers to steal your data and sell it for profit. Moreover, if you are subject to PCI-DSS you are even liable to substantial fines.Frequently asked questions
Intrusion detection systems (IDS) scan your network or your host and detect suspicious patterns, for example, suspicious traffic or suspicious files. Based on these patterns, they report intrusion attempts (successful or unsuccessful). Intrusion detection systems are not meant to protect your systems against intrusions.
Intrusion prevention systems (IPS) are intrusion detection systems (IDS) that can react to an intrusion immediately, for example, by blocking network traffic. The name may be misleading because they do not prevent an intrusion, simply react to it. To truly prevent intrusions, you should check if your systems have any vulnerabilities using a vulnerability scanner.
An intrusion detection system is a reactive system. It reacts to an attempt (successful or unsuccessful), leaving you very little time to do something about it. A vulnerability scanner is a proactive system. It helps you make sure there are no vulnerabilities that may lead to an intrusion.
If a successful web intrusion is reported by your intrusion detection system (or detected manually), you can use Acunetix to scan your website or web application to find the vulnerability that led to the intrusion. Acunetix will also help you learn how to fix that vulnerability. Acunetix is there to help you ensure that your intrusion detection system has as little work as possible.
