Acunetix – an Online Scanner for Your Web Security
Every business knows the importance of malware protection. Company computers are secured using virus scanners such as Kaspersky, F-Secure, Norton, AVG, Bitdefender, Virustotal, Metadefender, Trend Micro, or other. Antivirus software is also commonly used for company Android devices and other mobile devices. However, most businesses don’t realize that an antivirus engine is completely useless against malicious attacks that can even lead to such massive breaches as a leak of personal information for all citizens. Next to phishing, malware, and ransomware, the biggest threat to Internet security relates to assets that can be easily exploited because they are exposed to the public – websites and web applications. Unfortunately, vulnerabilities in such assets can only be discovered and mitigated using specialized software – web vulnerability scanners. Common cybersecurity tools such as antivirus programs, spyware removal tools, and firewalls are unable to help even a little bit. Acunetix is the pioneer in web vulnerability scanning – the first company ever to develop such a tool. It is also renowned for its high performance, high efficiency, unique scanning algorithms, ability to prove vulnerabilities, and a low number of false positives. If you have any web assets such as web applications, websites, or APIs, you need a vulnerability scanner. You need Acunetix.
The Importance of a Web Security Scan
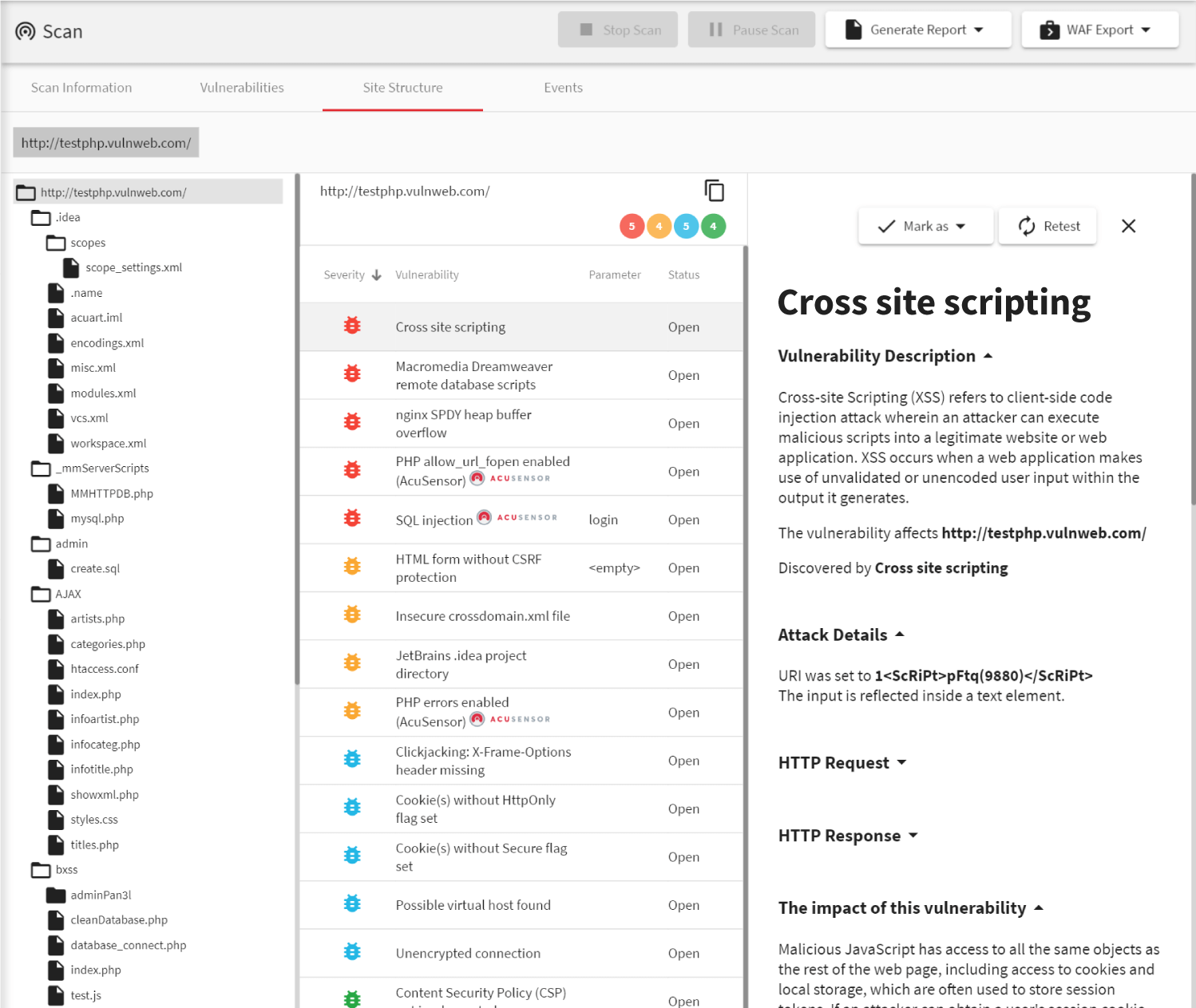
Web vulnerabilities can be just as dangerous as malware and phishing and sometimes even affect not only your business but also your clients. Therefore, web security software is of utmost importance to any business. Web security scanning imitates the actions of a hacker. A web vulnerability scanner attempts to exploit vulnerabilities in your websites and web applications, but does it in a safe way and shows you how it can be done.
- Vulnerabilities such as SQL Injections may let the attacker access your databases or even the operating systems of your web servers. From there, they may even gain complete control over other computers used by your business. This can happen even if you host your web assets on renowned platforms.
- Other types of vulnerabilities such as Cross-site Scripting (XSS) or Cross-site Request Forgery (CSRF) may endanger your customers. If your web application has an XSS vulnerability, attackers may use it, for example, to trick your clients into downloading malware or steal data from their machines. With CSRF, an attacker may cause your client to perform unsolicited actions on your website.
- Using popular web software exposes you even more. For example, both the WordPress engine and plugins have been the cause of many security breaches and security researchers keep finding new vulnerabilities related to WordPress all the time.
The Value of an Online Scanner
To save internal resources, many businesses select cloud solutions. The cloud-based version of Acunetix is able to detect exactly the same external vulnerabilities as an on-premises solution (available for Microsoft Windows, Linux, and macOS).
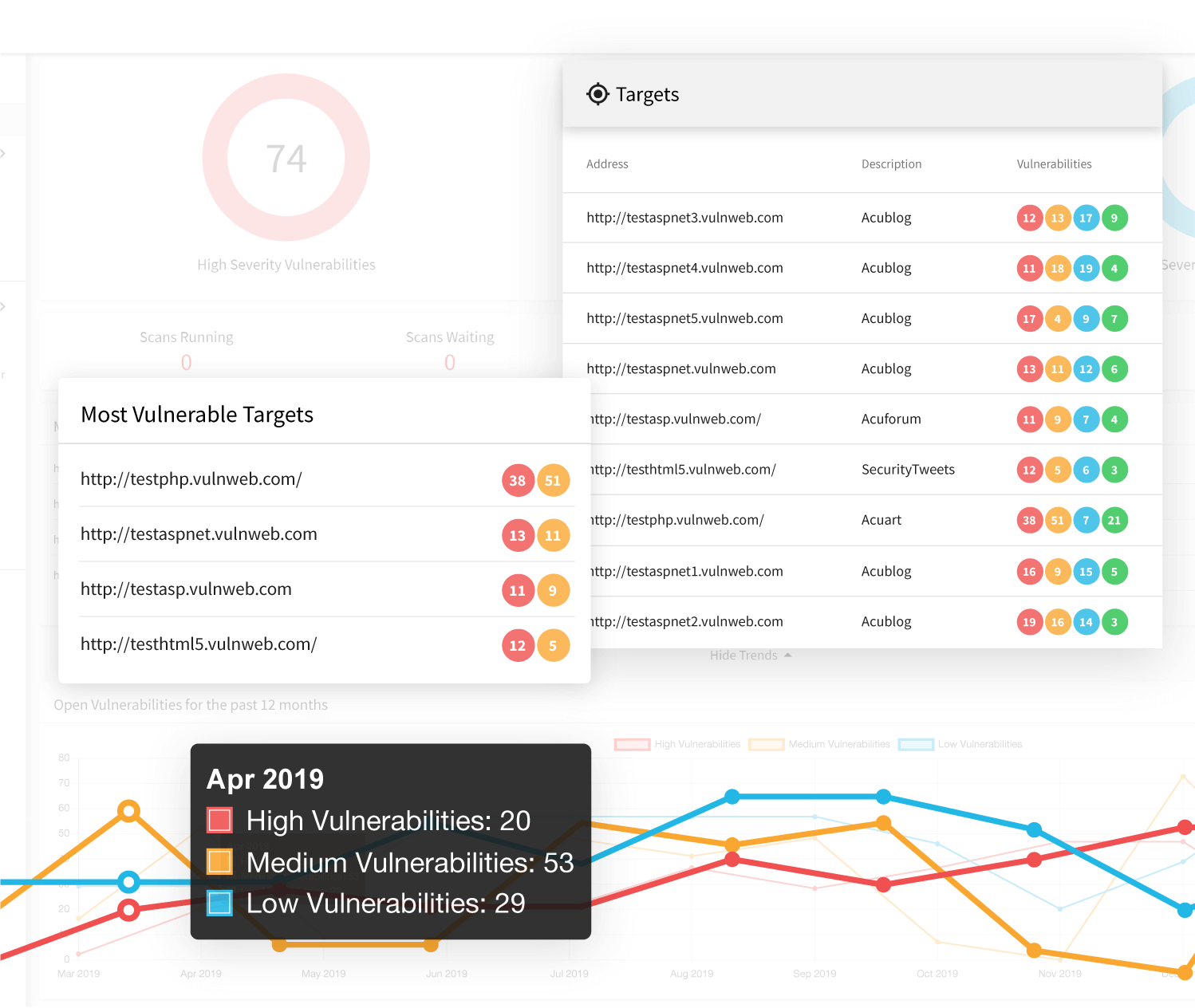
- Acunetix Online crawls and analyzes your website or web application to discover its structure, even if it’s very complex. It does not matter whether your web assets are based on an open-source solution such as WordPress, a commercial product, developed by a third party, or developed in-house. It does not matter, which technologies are used to build your website or web application. If a user can view a website using their Chrome, Firefox, or Internet Explorer, Acunetix can scan it.
- If Acunetix finds any vulnerabilities, it automatically assigns priorities. Therefore, you immediately know, which vulnerabilities you should focus on first and which pose the greatest danger to your business. Acunetix also provides detailed scan results as reports including explanations of vulnerabilities and remediation advice, which is important because you cannot remove web vulnerabilities the way that you remove malware.
- You can also use Acunetix to manage your vulnerabilities: track their remediation and retest. If your business uses an issue tracker such as Jira, GitHub, or GitLab, Acunetix can send issues directly to that tracker. If your business uses CI/CD tools such as Jenkins, you can even run quick scans in real-time during development.
Frequently asked questions
An online vulnerability scanning solution is much quicker to set up than an on-premises solution. A cloud scanner does not consume any local resources. You do not need to manually update an online solution or perform any maintenance on it.
To scan intranet websites and web applications using Acunetix Online you need to make them accessible via the Internet. You need to configure port forwarding on your local firewall and set up suitable rules so only Acunetix online has access to such sites.
See how to make internal web assets accessible from outside the internal network.
When you purchase Acunetix, you must decide whether you want to use Acunetix Online or Acunetix On-Premises. You cannot use them interchangeably with the same license key.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox