Just because you think your data is safe does not mean your database of sensitive organization information has not already been cloned and is resident elsewhere ready to be sold to the highest bidder. To make matters worse, only recently, it has been discovered that hackers are not simply selling your data; they’re also selling the fact that you have vulnerabilities to others be they hackers, industrial spies or terrorists.
It all sounds apocalyptic, doesn’t it? Well, rather than being an angel of doom, I’ll let the stats speak for themselves.
LEARN MORE: Hacking Software
TJX Companies Inc.,
TJX Companies, owners of T.J. Maxx, Marshalls, Winners, HomeGoods, A.J. Wright, and Bob’s stores fell prey to one of the worst web hacking incidents to-date. On the 17th January this year, the company disclosed that 40 million of their customers’ credit and debit card details were stolen. In parallel, federal credit union SEFCU published a similar warning that the personal details of 10,000 of its customers were compromised in the web hacking attack.
Another 60 banks including Citizen Union Savings Bank and Bank of America seem to have customers whose credit and debit cards have been breached in this attack.
Ben Cammarata, Chairman and Acting Chief Executive Officer of TJX Companies, stated that the nature of the hack is not known and two computer security experts are at hand examining the problem. The warning issued by SEFCU sheds greater light and states “A fraudster may have gained access to … card information through one of those entities in the payment network, including the merchant.”
SC Magazine reports that hackers used data from the breach to purchase goods in a number of states in the US, in Hong Kong and in Sweden.
A digest of the latest developments follows:
- According to 3WCAX-TV Website, the web hacking attack is expected to cost consumers one-point-five (M) million dollars. This article was published before law suits started sprouting.
- Brian Fraga, Standard-Times, reports that a class action lawsuit filed this week in U.S. District Court (Boston) against TJX. The amount of damages sought is undisclosed. According to SC Magazine, yesterday a West Virginia resident slapped another lawsuit and is suing TJX for $5 million.
- U.S. Rep. Ed Markey, D-Mass., chairman of the House Subcommittee on Telecommunications and the Internet, has called for the Federal Trade Commission to investigate the hacking, according to a eport today in the Boston Globe.
- Today, the Government of Canada, stated that it is launching an investigation into TJX and the data breach.
- Of note is that the hacking may have started in May 2006 and the breach was discovered only in December 2006 (and publicized in January 2007).
Hacking Universities
University systems are usually highly decentralized which makes it hard to ensure tight security. To the extent that one department may have deployed a hardened security infrastructure while others loll in lax measures making the whole system weak.
The following are some of the recent university hacks due to web application vulnerabilities:
- Last month, a hacker infiltrated a massive database from the University of California, Los Angeles, containing personal information (including social security numbers, dates of birth, home addresses and contact information) on 800,000 people in one of the worst computer breaches ever at a US university.
- In January 2007, the University of Arizona reported a web hacking breach happening November and December last year that effected several services according to the Privacy Clearing House. The number of effected records is as yet undisclosed.
- In December 2006, University of Colorado – Boulder experienced a web hacking attack that resulted in the theft of thousands of names and social security numbers – a total of 17,500 records were compromised.
- University of Texas, Dallas, reported in December 2006 that the data of 35,000 individuals (current students and alumni) was compromised. Social security numbers were exposed, according to the Privacy Clearing House.
Changing Trends in What Motivates Hackers
According to Zone-H, the top 50 attackers defaced a total of approximately 2.5 million websites all over the globe. According to the CSI/FBI Computer Crime and Security Survey 2005, one of the most dramatic findings was the exponential increase in website defacement experienced by their respondents: in 2004, 5% of the respondents experienced defacement while in 2005 that figure went up to 95%. Recent trends over the past 12 months show that there is a shift from such disruptive vandalism that gains notoriety towards theft of data that translates into profit. The report on 2006 is still to be published.
LEARN MORE: Ethical Hacking Software
Statistics
Since many organizations do not monitor online activity at the web application level, hackers have free reign and even with the tiniest of loop holes in a company’s web application code, any experienced hacker can break in using only a web browser and a dose of creativity and determination. It seems that most hack attacks are discovered months after the initial breach simply because attackers do not want and will not leave an audit trial. In web application attacks physical evidence (e.g., a missing database) is inexistent – hackers are interested in stealing the data and leaving it intact.
Recent research by a leading research firm shows that 75% of cyber attacks are done at web application level. Research at Acunetix corroborates this finding. Competing web application security organizations record similar data.
The Privacy Clearing House reports more interesting findings including the fact that over 100 million records have been compromised since February 2005. However this figure excludes the TJX episode of around 40 million records. Out of a total of around 140 million approximately 80 million were due to web hacking attacks.
The Cost of Web Hacking
The costs of hack attacks to any organization are extensive with possible financial burdens that may result in closure:
- Loss of customer confidence, trust and reputation with the consequent harm to brand equity and consequent effects on revenue and profitability;
- Possible loss of the ability to accept certain payment instruments e.g. VISA, Mastercard
- Negative impact on revenues and profits arising from any falsified transactions and from employee downtime;
- Website downtime which is in effect the closure of one of the most important sales channels for an e-business;
- The expenditure involved in repairing the damage done and building contingency plans for securing compromised websites and web applications; and,
- Legal battles and related implications from Web application attacks and lax security measures including fines and damages to be paid to victims.
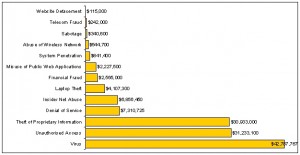
The figure above shows the total losses as reported by the 2005 CSI/FBI Annual Computer Crime and Security Survey.
The total losses per category of breach (valid only for the US) is reported to be over $130 m for the 639 respondents willing and able to estimate their losses. The Survey authors also state that while explicit costs (such as costs of reinstalling software and reconfiguring computer systems) is more accurately accounted for by respondents, implicit costs (such as lost future sales due to negative media coverage following a breach) is more difficult to account for and are largely not represented in the loss numbers reported here.
Now does it sound apocalyptic? I believe there is serious need for all to worry.
Acunetix Web Vulnerability Scanner
Learn more about Acunetix Web Vulnerability Scanner and how the solution helps to regularly audit your website and web applications for vulnerabilities to web hacking attacks.




