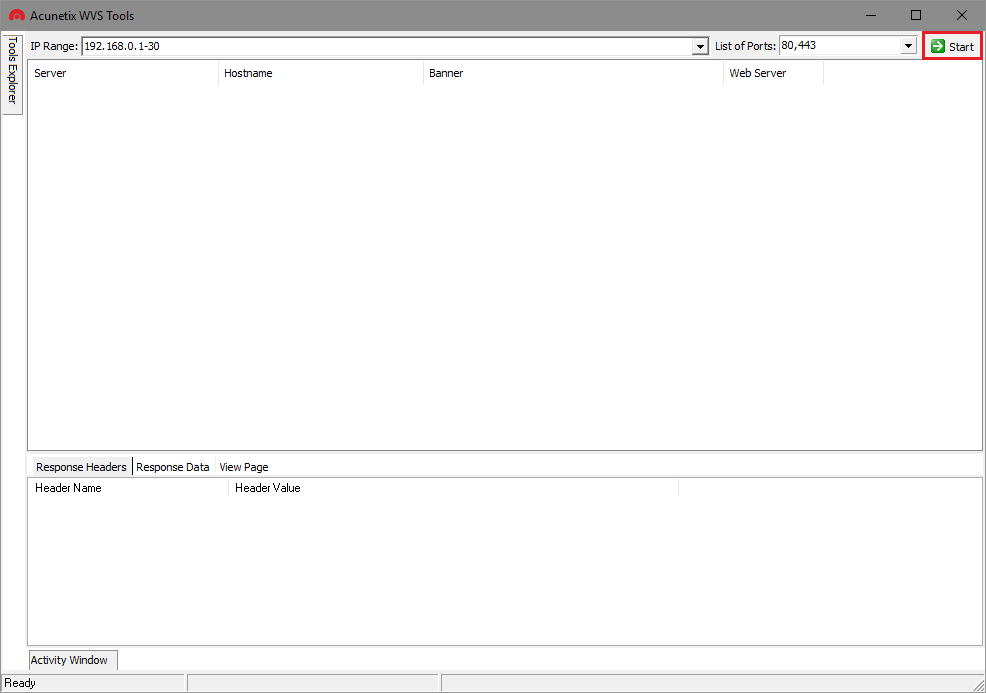
The Target Finder is a tool that forms part of the Acunetix Manual Tools suite (available to download for free). The Target Finder allows you to run a port scan to discover web servers running on a given IP address, or a range of IP addresses.
You can start using the Target Finder by launching the Acunetix Tools application, and selecting the Target Finder from the Tools Explorer.

The top pane in the Target Finder is where you’ll see results of the port scan. The bottom pane displays the HTTP response headers and data received from the server.
Find web servers in an IP address range
In order to start port scanning an IP address range, enter the IP address range in any of the following formats in the IP Range field and click the Start button to begin the port scan.
example.com Scan a host by DNS hostname192.168.0.1 Scan a host by IP address192.168.0.1-30 Scan all hosts between two IP addresses192.168.0.0/24 Scan all hosts in a subnet (CIDR format)
| example.com | Scan a host by DNS hostname |
| 192.168.0.1 | Scan a host by IP address |
| 192.168.0.1-30 | Scan all hosts between two IP addresses |
| 192.168.0.0/24 | Scan all hosts in a subnet (CIDR format) |
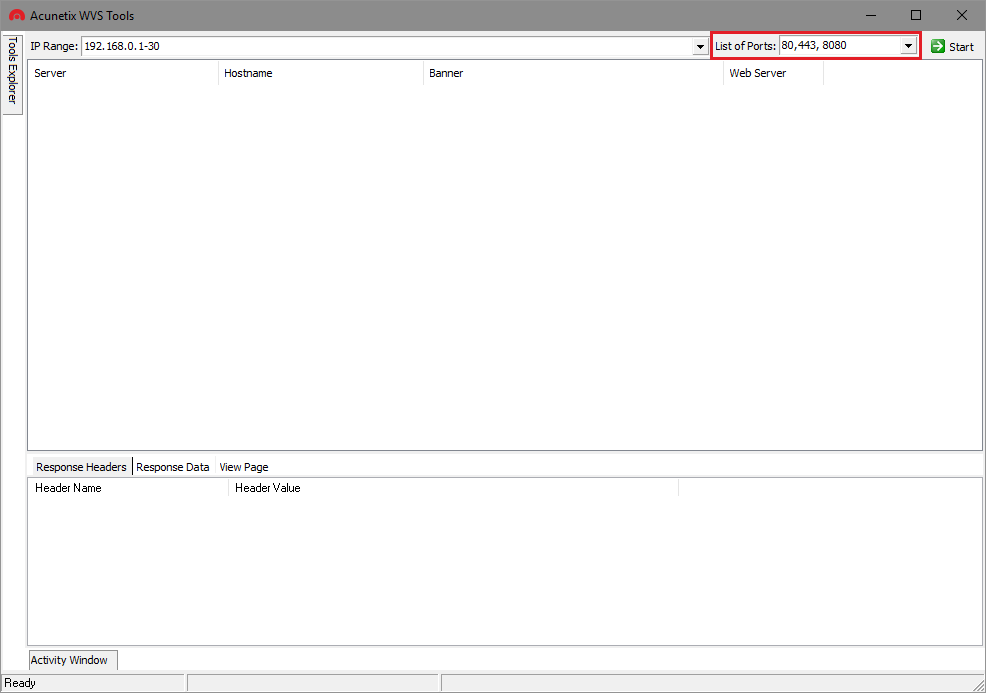
Find web servers on non-standard ports
The default ports the Target Finder will scan are port 80 and port 443, however you can easily change or expand this port range to fit your needs by modifying the List of Ports field. The List of Ports field accepts a comma-separated list of ports.
Analyzing results
Discovered web servers are displayed as soon as they are discovered in the bottom pane. The server’s hostname, banner and type are also retrieved.
You can right-click the discovered web server to send custom requests using the HTTP Editor, as well as export the list of discovered web servers as a CSV file.
Acunetix is an automated web application security scanner and vulnerability management platform. In addition, Acunetix also provides a suite of manual pentesting tools that allow users to quickly and easily confirm and take automated testing further.
Get the latest content on web security
in your inbox each week.




