Acunetix WVS is equipped with the Acunetix Client Script Analyzer (CSA) which is a fully automated JavaScript parsing engine that overcomes the general need for manually crawling and following JavaScript links.
To execute its vulnerability audits, Acunetix WVS simulates the manual intervention of a penetration tester (ethical hacking) by first “crawling” the website and web applications identifying its directory structure.
Any standard web browser has a JavaScript engine that interprets and executes (client-side) any JavaScript embedded in HTML pages. Acunetix CSA works in the same manner as such a JavaScript engine.
When a document is loaded within a web browser, HTML tags are parsed to render visible the various elements of the page to the user. At the same time, any JavaSscript scripts are executed by the JavaScript engine within the browser allowing events and behaviours to become active within the page presented to the user. Some of these events and behaviours require user intervention, whereas others do not (i.e., implicit scripts or scripts which execute without user intervention).
Similarly, the Acunetix CSA will load a page parsing the HTML code contained therein and executing all events and behaviours found on the crawled page. Acunetix CSA will simulate almost all interfaces which Microsoft’s Internet Explorer exposes to its JavaScript engine, and this gives it almost the same automated capabilities that any web browser has.
The main advantage of Acunetix WVS is that whereas most web-application scanners stop at parsing the JavaScript on a webpage, the CSA will actually execute the scripts. Such execution is critical since it allows greater and more automation, in-depth vulnerability checks on the identified JavaScripts and AJAX web applications. Thus, Acunetix WVS is able to find the many weaknesses that lie deep in the code of web pages.
The following is a simple HTML example of the sequence of events as processed by the Acunetix CSA:
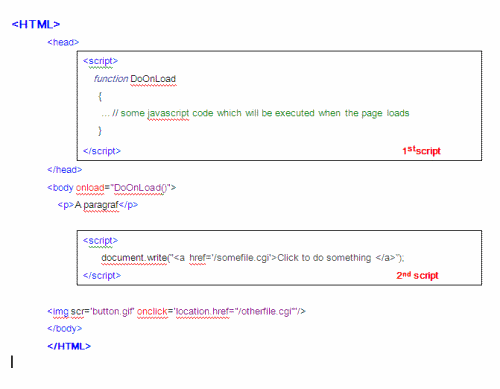
First the Acunetix CSA will parse the HTML code to construct the DOM representation of the page yielding a skeletal structure of the page that shows the sequence in which the tags must be read and executed.
CSA will identify the exact location of all various scripts contained therein and the relevant references to elements, events and behaviours. CSA will execute all the scripts found on the various pages – both those that are activated through user intervention (e.g., OnClick, OnChange) and those that are executed by the system (e.g., OnLoad, OnUnLoad). Acunetix CSA will execute implicit scripts during HTML parsing since these have an effect on the parsing itself (because these scripts actually determine the structure of the page).

After parsing the page, CSA will activate all the remaining events that were bound during the execution of the script. These events are activated following the logical web browsing order. For example, a user cannot press a button until the page is loaded; therefore ‘onclick’ will always follow ‘onload’.
To accurately detect which AJAX web applications contain vulnerabilities, Acunetix WVS launches its attacks by sifting through the code (as explained above) in reality emulating a hacker. Hackers do not stop at simply observing the code but would actually execute it even going as far as making the ‘necessary’ modifications to cause misbehaviour. The efficiency of an Acunetix vulnerability scan is based upon the same techniques which a hacker uses to manipulate the AJAX structure for Cross-site Scripting (XSS), SQL Injection, traffic monitoring, session interception, and others.
AJAX-based web applications are rendered in a web browser in modular style by which various single elements of and events in a web page can be loaded and refreshed individually. Thus such applications present a wider window of opportunity for data insertion and manipulation. A thorough audit with Acunetix WVS significantly reduces such associated risks because CSA will parse and execute all scripts. Developers are presented with a more accurate representation of the vulnerabilities contained in their code and may then proceed to make the necessary changes and fixes.
Without the correct interpretation and execution of JavaScript in AJAX applications, a web vulnerability scanner will only limit itself to testing a web application in a global manner instead of its individual components.
Scanning for XSS Vulnerabilities with Acunetix WVS
To check whether your website has cross site scripting vulnerabilities, download the 14-day Trial of Acunetix WVS. This version will scan any website / web application for XSS vulnerabilities and it will also reveal all the essential information related to it, such as the vulnerability location and remediation techniques. Scanning for XSS is normally a quick exercise (depending on the size of the web-site).



