Reginaldo Silva recently uncovered a very interesting bug affecting Facebook (and received $33,500 for this discovery). The bug is caused by improper handling of XML documents in OpenID implementations causing XML External Entity Expansion vulnerabilities. He mentioned in his article that many OpenID implementations/libraries are affected by this bug.
I was curious to learn more about this bug and check if it’s possible to detect this type of bug automatically with Acunetix Web Vulnerability Scanner. Reginaldo mentioned that he initially found an XXE OpenId bug in Drupal version 7.15 (CVE-2012-4554) so this was my starting point.
I downloaded and installed Drupal version 7.15 and compared the source code with Drupal version 7.16 to see how the bug was fixed. Fortunately there were not many differences between v7.15 and v7.16 so I quickly found this piece of code that is fixing the problem.
So, when parsing XRDS XML documents Drupal was not properly parsing the XML document it received an was vulnerable to an XML External Entity Expansion vulnerability.
In case you don’t know what XRDS is, here is a quote from Wikipedia:
XRDS (eXtensible Resource Descriptor Sequence) is an XML format for discovery of metadata about a web resource – in particular discovery of services associated with the resource, a process known as service discovery. For example, a website offering OpenID login can resolve a user’s OpenID identifier to an XRDS document to discover the location of the user’s OpenID service provider.
This bug is affecting Drupal installation version 7.15 where OpenID authentication plugin was enabled. When OpenID authentication is enabled Drupal users can login by providing an OpenID URL. It looks like this:
At this point the problem should be pretty obvious. An attacker can provide an OpenID XRDS URL to a server controlled by the attacker. When Drupal will visit this URL, the server returns an malicious XML that contains an XXE. Drupal will parse this XML and expand the XXE entity causing the vulnerability. At this point the attacker can read any file from the web server and even execute PHP code in some particular situations.
Now I understood the vulnerability but I wanted to detect it automatically. In Acunetix WVS, AcuMonitor service helps detect more complex issues like this one.
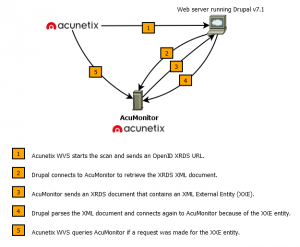
AcuMonitor can automatically detect SSRF (Server Side Request Forgery) vulnerabilities and therefore the scanner knows when the scanned web application is making a remote HTTP connection. So, the next step was to configure AcuMonitor to return a malicious XRDS XML document. The document will include an XXE entity and the scanner can later query AcuMonitor if the web application expanded the entity. I’ve made a simple diagram to explain how the process works:
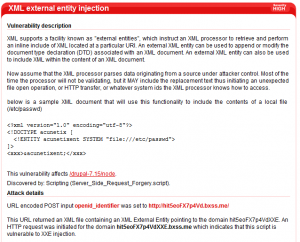
So, I’ve scanned the Drupal version 7.15 installation to see what it finds and as expected it reported 2 vulnerabilities (one SSRF vulnerability and one XXE vulnerability) as you can see below.
However, this check does not apply only to Drupal. If AcuMonitor is enabled, the scanner should now be able to automatically discover other OpenID XXE bugs in vulnerable web applications.
Get the latest content on web security
in your inbox each week.