WordPress, the content management system powering north of 28% of websites on the Internet, is certainly no stranger to providing timely security patches to its hundreds of millions of users when security researchers report them. This time however, things took a slightly different turn — Enguerran Gillier, a security researcher discovered and disclosed a Cross-site Flashing (XSF) vulnerability in the WordPress core affecting all WordPress versions going back a whole 2 years, including the very latest security release of WordPress (version 4.8.2 at the time of writing). The same security researcher had also previously reported similar vulnerabilities in a Facebook bug bounty program.
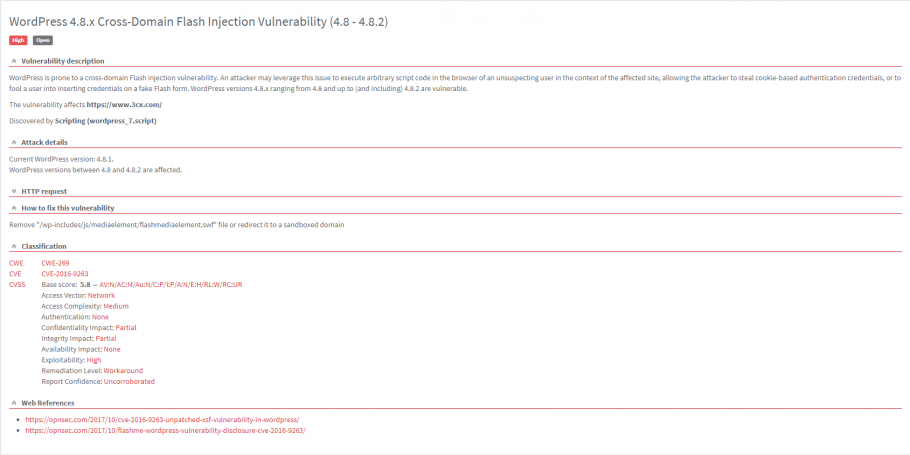
The vulnerability is similar to a Reflected Cross-site Scripting (XSS) vulnerability. An attacker could execute arbitrary Flash code within the WordPress security sandbox. This means that an attacker can craft code to send a request to any URL within the domain WordPress is hosted on, using the victim’s Cookies. While the attacker may not manipulate the DOM, if the victim has Adobe Flash enabled, the attacker can send requests and read responses to obtain WordPress CSRF tokens and perform actions on behalf of the user. If that user happens to be an administrator, this includes the possibility of installing malicious plugins which the attacker may then escalate to a much more grievous attack.
Unlike most WordPress vulnerabilities, this does not come with a recommendation to patch since no patch is yet available. Even though the researcher behind this vulnerability has disclosed this bug to the WordPress core maintainers over a year ago (August 2016), a fix has not been released yet.
Luckily, the fix is as simple as deleting or restricting access to the vulnerable file located at /wp-includes/js/mediaelement/flashmediaelement.swf. This file is just a Flash fallback for embed videos which are not hosted on a streaming website such as YouTube or Vimeo.
In the build released on the 17th October 2017, Acunetix now automatically tests for this Cross-site Flashing (XFS) vulnerability as part of its hundreds of WordPress core and WordPress plugin tests. Both Acunetix On-Premises and Acunetix Online can now detect this vulnerability automatically.
Get the latest content on web security
in your inbox each week.




