 The year debuted with ‘Operation Aurora‘: Google and over 30 other companies were hit by a spear phishing attack which resulted in theft of intellectual property from Google and probably other companies. Spear phishing is a targeted form of phishing in which an e-mail message might look like it comes from your employer, or from a colleague who might send an e-mail message to everyone in the company, such as the head of human resources or IT. The attackers used an Internet Explorer 6 zero day vulnerability.
The year debuted with ‘Operation Aurora‘: Google and over 30 other companies were hit by a spear phishing attack which resulted in theft of intellectual property from Google and probably other companies. Spear phishing is a targeted form of phishing in which an e-mail message might look like it comes from your employer, or from a colleague who might send an e-mail message to everyone in the company, such as the head of human resources or IT. The attackers used an Internet Explorer 6 zero day vulnerability.
Spear phishing is very hard to protect against, each company is more or less vulnerable to this threat because it targets the human factor. However, what I don’t understand is why Google’s employees are using Internet Explorer 6 as their primary browser. Not why they are using Internet Explorer. Why they are using Internet Explorer 6?
Internet Explorer was released in 2001 and Secunia lists 184 known Vulnerabilities for this product. If Microsoft with its Security Development Lifecycle (SDL) and billions of dollars in bank cannot secure ONE single piece of code 9 years later, then something is wrong. What can you expect from other companies?
A few days ago, Network Solutions announced that several hundred websites hosted on its infrastructure were hacked/defaced because hackers had broken into its servers by exploiting a file inclusion vulnerability. Network Solutions is one of the top five Internet domain name registrars.
Yesterday, I’ve read about Tor’s servers being breached. It seems that two of the seven Tor directory authorities were compromised, along with metrics.torproject.org. Roger Dingledine wrote:
It appears the attackers didn’t realize what they broke into — just that they had found some servers with lots of bandwidth.
So, the attackers didn’t even target Tor, they just happened to hack two of their servers, probably using some automated tool. This makes me think that Tor had some serious vulnerabilities.
Yesterday, I was also browsing some random website and I’ve reached its 404 (page not found) page by mistake. This particular page was a custom 404, displaying a bunch of Google ads.
This page looked familiar to me and I remembered that I’ve read about it in a blog post from RSnake. The blog post was entitled 1&1 Internet Customers Vulnerable to XSS. So, if your website was hosted by 1&1 (another one of top five Internet domain name registrars) and you didn’t manually set your own custom 404 page, 1&1 will gladly prepare one for you. The only problem is that this custom 404 page was/is vulnerable to XSS. This means that all the sites that have this custom 404 page are vulnerable to XSS.
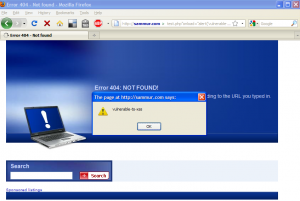
Here are two random sites hosted on 1&1 that are affected by this vulnerability:
http://sammur.com/test.php%22onload=%22alert%281%29
http://googleceltic.com/test.php%22onload=%22alert%281%29
This vulnerability was reported on December 30th, 2007 and 1&1 knew about it (see the comments from RSnake’s page). And still, 2+ years later, its customers are still vulnerable to XSS. Not because their own sites are vulnerable but because 1&1 wants to make some easy money with Google ads and cannot even fix a simple XSS vulnerability.
If Google, Microsoft, Network Solutions, Tor, 1&1 cannot implement proper security measures, then something is wrong.
Security is hard, too hard in my opinion.
Get the latest content on web security
in your inbox each week.



