Aside from better scanning of Java/J2EE web applications, Acunetix WVS version 10 comes with improved support for web applications built using the popular framework Ruby on Rails.
A lot of new Rails specific tests were added in the new version. For example, many Rails developers use Rails scaffolding. Rails scaffolding is a quick way to generate some of the major pieces of a Rails application. When scaffolding is used, Rails will automatically create the models, views and controllers for a new resource in a single operation. Output formats are handled in the controller automatically. JSON and XML are natively supported by Rails. Sometimes developers use scaffolding but don’t properly restrict access to all the APIs generated automatically by Rails. In this case, sensitive information is leaked via the auto-generated APIs.
Acunetix WVS can automatically identify resources and look for potentially sensitive information leakage, look for Controller actions that were left unprotected and other similar problems.
In this website scan, the scanner found some Rails resources and figured out possible actions for their controllers. It found that it’s possible to list all clients by requests /clients.json and the information returned contains possible sensitive information (such as email addresses). It also figured out that it’s possible to edit existing posts and to create new posts by using a url like /posts/6/edit (to edit) and /posts/new (to create a new post). It issued various alerts for these cases but some of these alerts require manual user confirmation because the scanner determines automatically if this is intended behaviour or not.
Rails applications often use a large number of Gems. Sometimes these Gems have critical security vulnerabilities. Acunetix WVS version 10 added various checks for important vulnerabilities in widely used Gems.
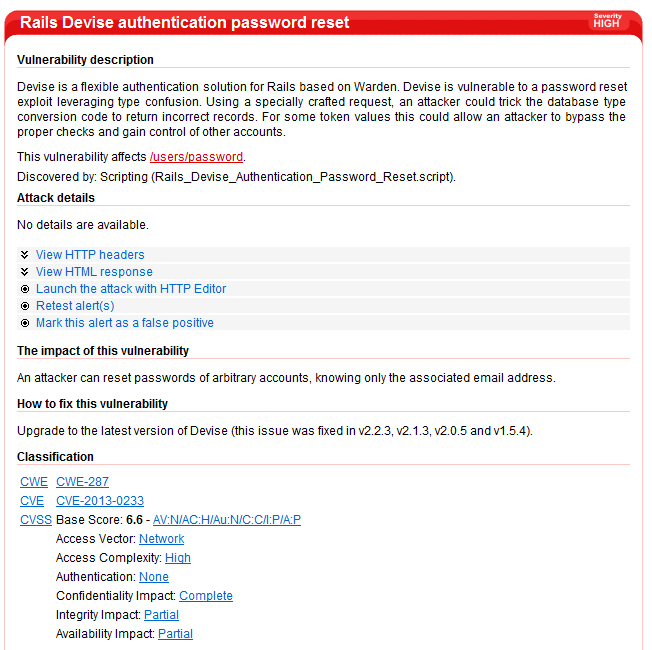
As an example, Devise is a flexible authentication solution for Rails based on Warden. Many Rails applications use this framework. In the scan below, the scanner figured out that this Rails application uses Devise for authentication and looked for known issues with Devise. It found one critical vulnerability affecting older versions for Devise:
In the end, let’s talk about an improved test. Each Ruby on Rails web application contains a secret token (usually stored in the file secret_token.rb). This token secret_token is used to sign cookies that the application sets. Acunetix WVS is looking for Rails applications that use a weak/known secret token. I was thinking that in production sites we will not find such vulnerabilities. However, this turned out to be false, since we found this issue again and again and in version 10 we’ve improved this test by adding a much larger dictionary of weak secrets, adding possible secrets by using words from the page, the hostname and the site name.
Get the latest content on web security
in your inbox each week.