MANAGE YOUR WEB SECURITY WITH
Acunetix Vulnerability Scanner | Accurate Vulnerability Scanning
Improve Your Web Application Security with the Acunetix Vulnerability Scanner
Acunetix is not just a web vulnerability scanner. It is a complete web application security testing solution that can be used both standalone and as part of complex environments. It offers built-in application and website vulnerability assessment and vulnerability management, as well as many options for integration with market-leading software development tools. By making Acunetix one of your security measures, you can significantly increase your cybersecurity stance and eliminate many security risks at a low resource cost.
Vulnerability Scanning Automation and Integration
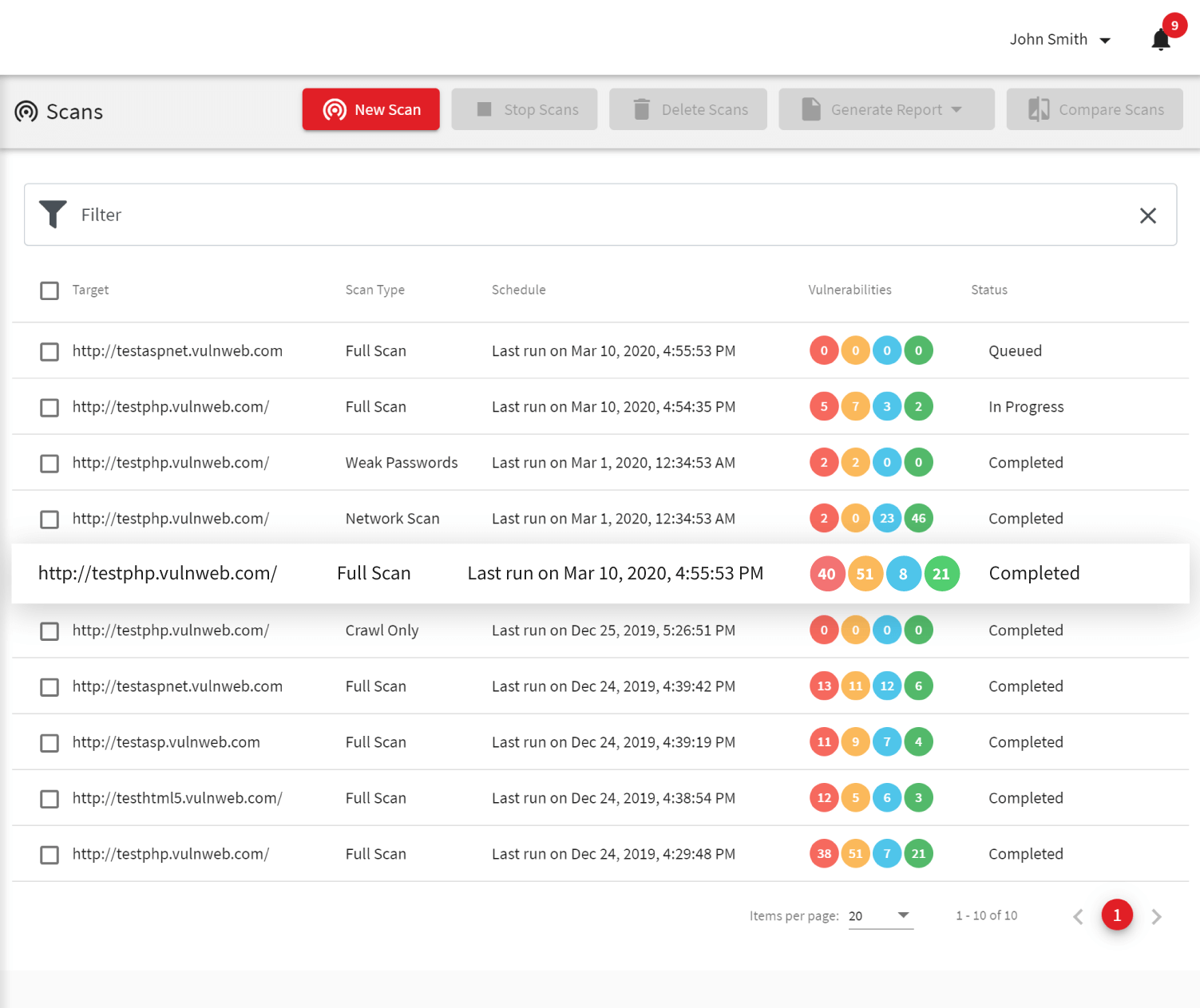
To save resources, ease remediation, and avoid late patching, enterprises often aim to include web vulnerability tests as part of their SecDevOps processes. Acunetix is one of the best DAST tools for such a purpose due to its efficiency in both physical and virtual environments.
- Acunetix integrations are designed to be easy. For example, you can integrate Acunetix scans in your CI/CD pipeline with tools such as Jenkins in just a few steps.
- For effective vulnerability management, you can also use third-party issue trackers such as Jira, GitLab, GitHub, TFS, Bugzilla, and Mantis. For some issue trackers, Acunetix also offers two-way integration, where the issue tracker may automatically trigger additional scans depending on the issue state.
- Acunetix vulnerability scanner offers its own API that you can use to connect to other security controls and software developed by third parties or in-house. In the case of enterprise customers, Acunetix technical experts will help you integrate the tool within atypical environments.
Fast, Accurate, and Scalable Web Vulnerability Scanner
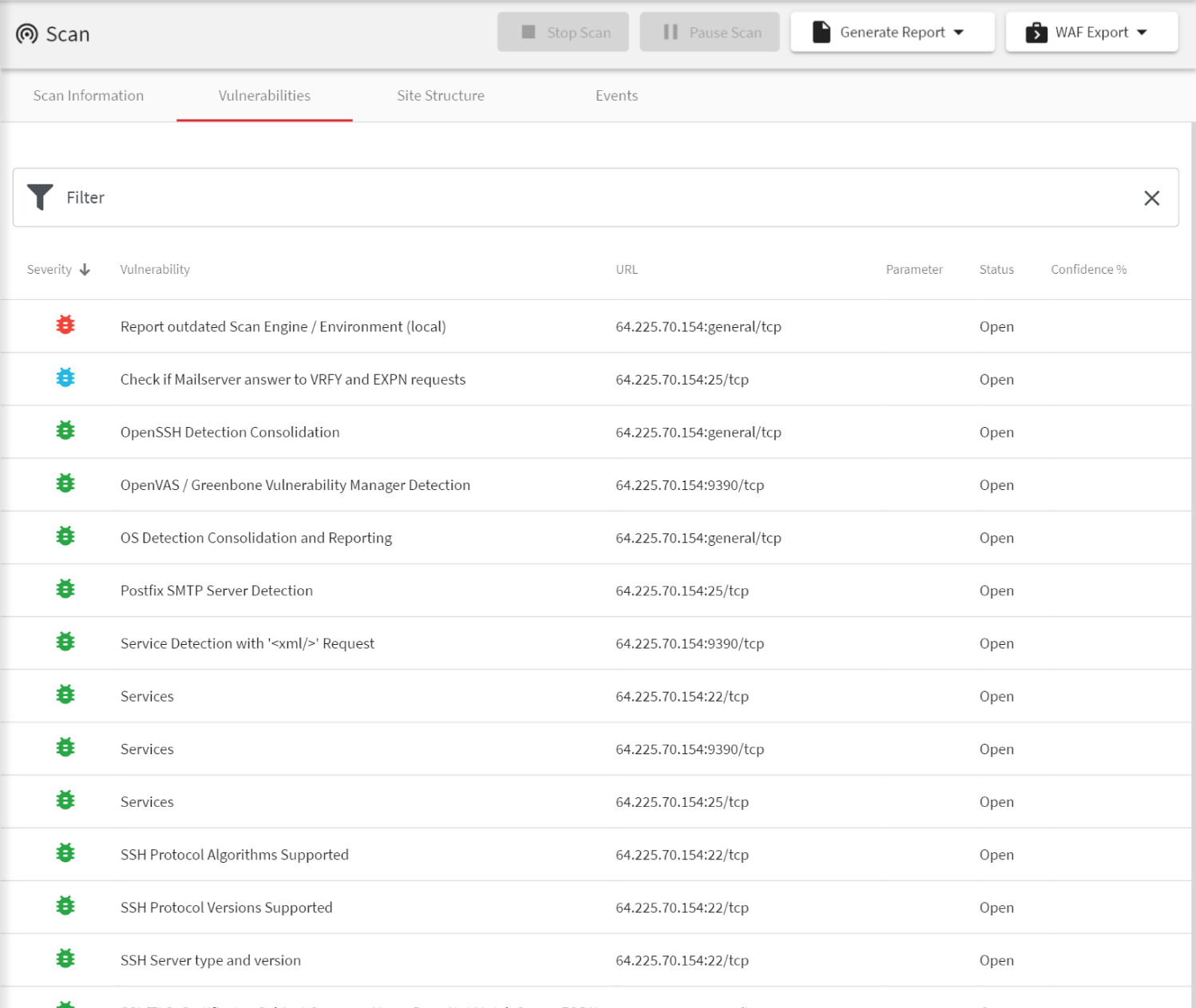
Acunetix is the first web vulnerability scanner on the market that is constantly being improved since 2005. It is a highly mature, specialized vulnerability scanner developed by web security testing experts. Such specialization made it possible to build a solution that is more effective than many bundled tools.
- The Acunetix vulnerability scanning engine is written in C++, making it one of the fastest web security tools on the market. This is especially important when scanning complex web applications that use a lot of JavaScript code. Acunetix also uses a unique scanning algorithm – SmartScan, with which you can often find 80% vulnerabilities in the first 20% of the scan.
- The speed goes in line with very high vulnerability discovery effectiveness. Acunetix is also known for its very low false-positive rate, which helps you save resources during further penetration testing and lets your analysts focus on new vulnerabilities. Acunetix also provides proof of exploit for many vulnerabilities.
- To increase web scanning efficiency, you can use multiple scanning engines deployed locally. Engines can work both with the Acunetix on-premises and cloud version.
Get Added Value From Your Website Vulnerability Scans
Acunetix is available in versions suited to different customer needs. It can be deployed locally on Linux and Microsoft Windows operating systems, but you can also use it as a cloud product to save your local resources.
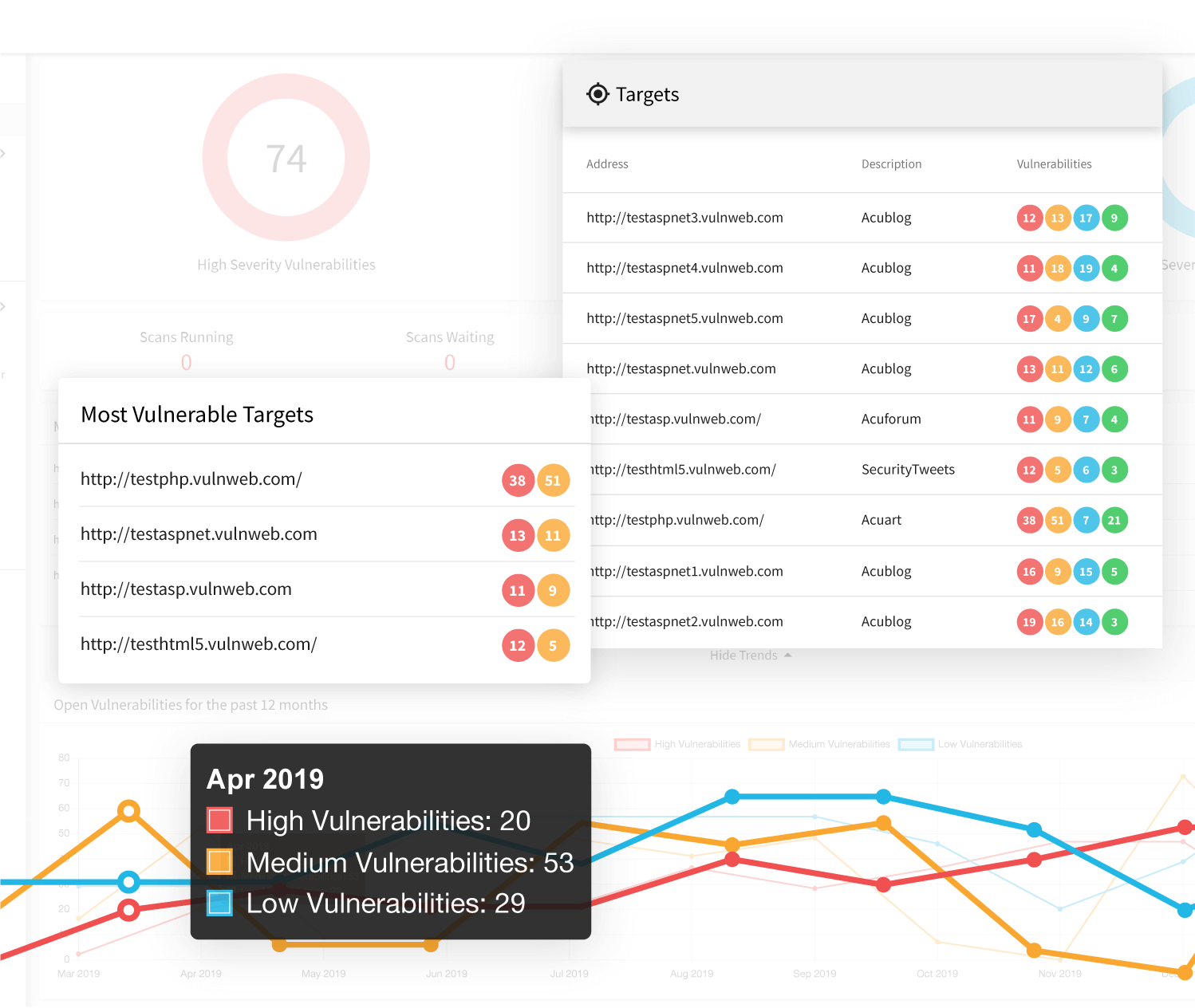
- In addition to web application vulnerabilities, such as SQL Injections and Cross-site Scripting (XSS), Acunetix helps you discover other security threats. This includes web server configuration issues or misconfigurations, unprotected assets, malware, and other security threats listed in OWASP Top 10.
- To protect your key assets, you can use the unique AcuSensor IAST technology for PHP, Java, or .NET. This technology helps you remediate by making it easier to pinpoint the cause of the security hole.
Frequently asked questions
Vulnerability scanning is the only automatic way to protect your website or web application from malicious hacker attacks. In addition, you should do manual penetration testing after a vulnerability scan. You should use web application firewalls only as temporary protection before you can fix vulnerabilities.
Read more about vulnerability scanning and penetration testing.
A vulnerability scanner sends special data to your website or web application – the type of data that a malicious hacker would send. However, it does it in a safe way. If the response from your website or web application shows that it can be hacked, the vulnerability scanner reports it to you and tells you how to fix it.
Learn how to set up the vulnerability scanner to scan a test web application.
You should scan your website or web application every time that you change it. However, if you use ready-made web applications such as WordPress, some plugins may be updated automatically and you do not always know if someone else is introducing changes. Therefore, we recommend that you run a full scan every week and a quick scan (incremental scan and/or high severity scan) every day.
We believe that Acunetix is the best vulnerability scanner because it is the most automated, the most efficient, and the most accurate scanner on the market. If you want to find out for yourself, test it along with other scanners.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox