A security researcher Youssef Sammouda (Samm0uda) recently discovered a critical CSRF (Cross-site Request Forgery) security vulnerability on Facebook. This security issue could have been used to take over any Facebook user account. Samm0uda reported the bug on January 26 and Facebook fixed it just 5 days later. On February 12, Facebook awarded Samm0uda with $25,000 bounty for finding and reporting this issue. Seemingly, nobody exploited the vulnerability before it was fixed.
Potential CSRF Impact
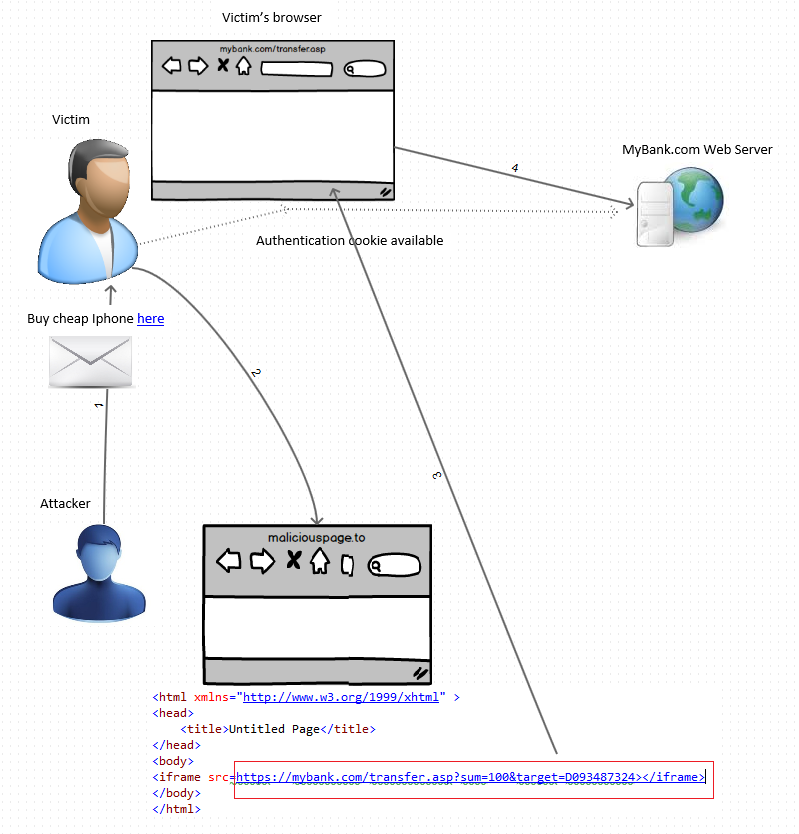
For the attack to be successful, the attacker would have had to trick a user into visiting a malicious URL. The URL could have been generic, so it could have been sent to millions of users at the same time. Also, the URL domain would have been facebook.com, so it would have been easy to trick a Facebook user into believing that this is a legitimate address.
Samm0uda demonstrated the following potential consequences of such an attack:
- Posting content on user’s timeline
- Removing the user’s profile picture
- Deleting the user’s Facebook account (the user must be tricked to enter their password)
- Taking over the Facebook account (the user must visit two URLs, not one)
Attack Vector Analysis
The CSRF vulnerability was discovered by Samm0uda in the https://www.facebook.com/comet/dialog_DONOTUSE/?url=<url> endpoint. If you supplied another endpoint as <url>, a POST request would have been made to it and a CSRF token fb_dtsg would have been added to the request body.
For example, according to Samm0uda, the following code would delete the user’s profile picture:
https://www.facebook.com/comet/dialog_DONOTUSE/?
url=/profile/picture/remove_picture/%3fdelete_from_album=1%26profile_id={TARGET_ID}Find Your Vulnerabilities
The bigger your application code, the more chances of security risks. For example, Facebook learns about hundreds of vulnerabilities annually just from third parties. Samm0uda alone received 16 bounties from Facebook just in January and February for reporting security issues.
This vulnerability proves once again, how dangerous CSRF attacks can be and how important it is to protect yourself against them. To check your website or web application for vulnerabilities, you can use the Acunetix vulnerability scanner, which includes a CSRF scanner.
Get the latest content on web security
in your inbox each week.