Online Vulnerability Scanner
If your business is looking for a comprehensive product to improve your web application security, the Acunetix vulnerability assessment and vulnerability management solution based on the leading-edge web vulnerability scanner is also available online. The Acunetix online solution offers all the functionality of the on-premises security scanner, not just vulnerability detection.
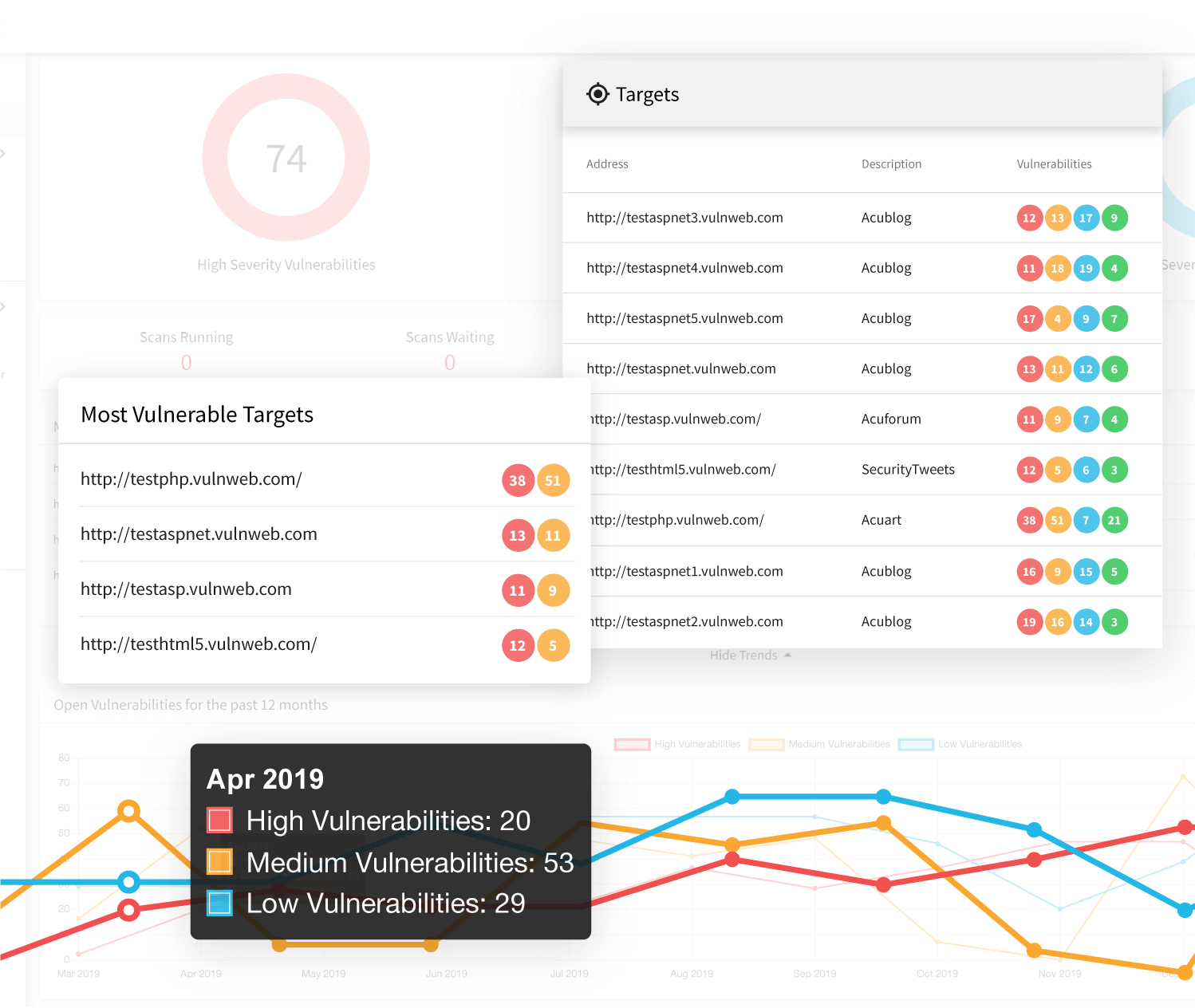
Integrate Acunetix Vulnerability Scanner within Your SDLC
The key focus of Acunetix is integration within your processes. Acunetix is built to become part of your complex environment so that you don’t waste resources on managing web vulnerabilities separately. Additionally, Acunetix satisfies the needs of developers, managers, and executives by providing specialized scan reports including security assessment and compliance reports such as PCI DSS and HIPAA.
- You can easily and quickly integrate Acunetix with market-leading issue trackers such as Jira, GitLab, GitHub, Mantis, Bugzilla, and Microsoft TFS. Acunetix converts discovered security vulnerabilities into manageable issues so you can include them in regular remediation processes.
- You can also include Acunetix scans in SecDevOps pipelines by easily integrating the scanner with market-leading CI/CD tools like Jenkins. Because Acunetix is built for performance, it won’t have a negative impact on your build times.
- Acunetix has import and export capabilities for various other products including web application firewalls, penetration testing tools, other scanning tools, and more.
Benefit from High-Performance Vulnerability Scanning
One of the distinguishing features of Acunetix’ vulnerability assessment and scanning is that it is developed with speed in mind. Each new version further improves performance, especially within large and complex security testing environments. High performance vulnerability scanning also goes in line with high detection rates and a very low number of false positives as well as a wide range of detected security issue types.
Web Application Security at its best: Network, SaaS, Web App, and more…
- The Acunetix core is built using C++. This low-level language helps the scanner achieve higher speed than competing products developed using high-level languages.
- The Acunetix scanner uses techniques to limit the number of requests as much as possible, which helps you reduce the network and web server load, while effectively idtentifying the attack surface and associated vulnerabilities in web applications online. The scanner is also continuously improved to further reduce and prioritize requests.
- In addition to typical web vulnerabilities such as SQL Injections, Cross-site Scripting (XSS), and other OWASP Top 10 issues, Acunetix dast functionality also tests for misconfigurations, weak passwords, issues related to the web server software, TLS/SSL vulnerabilities, and more.
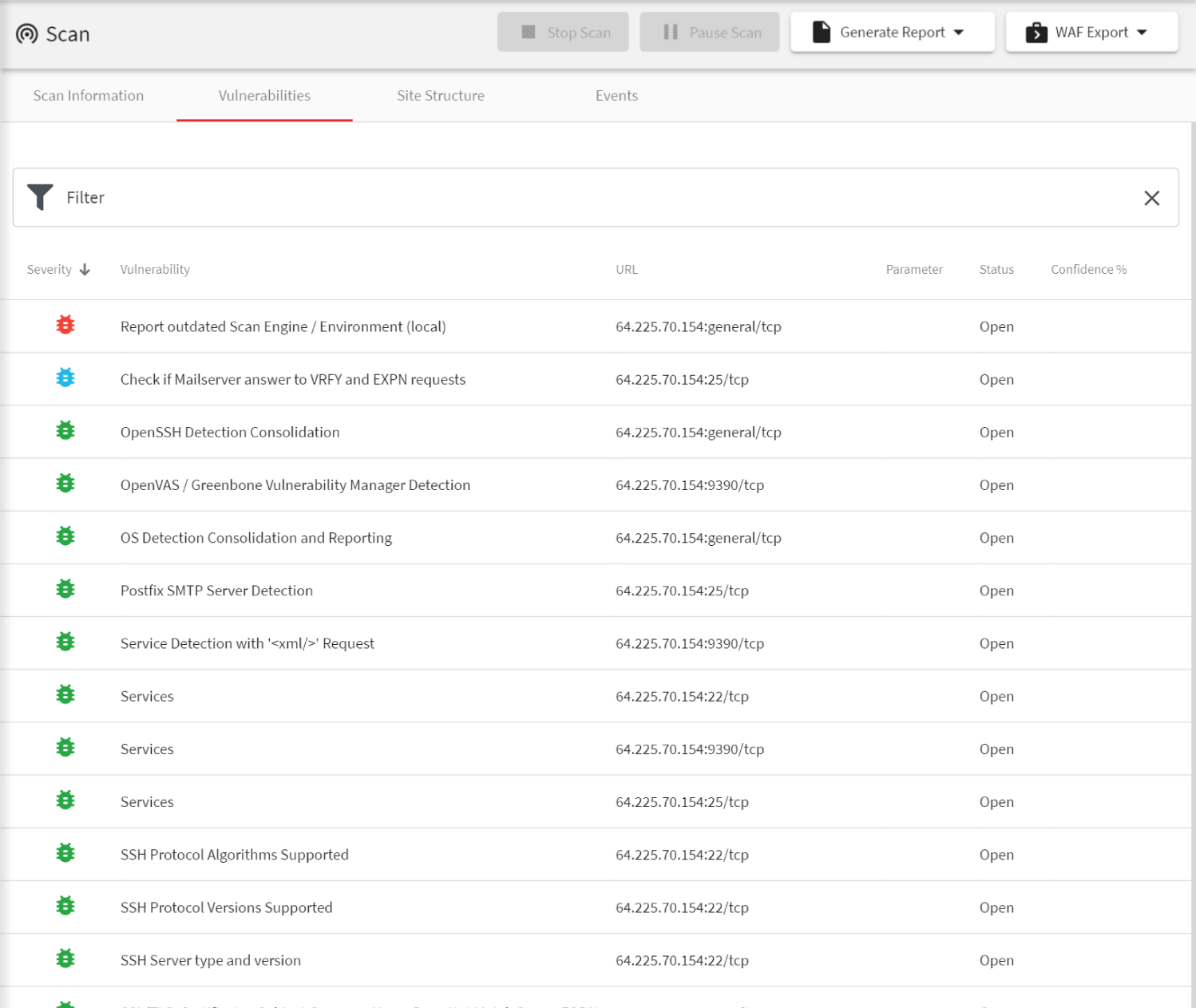
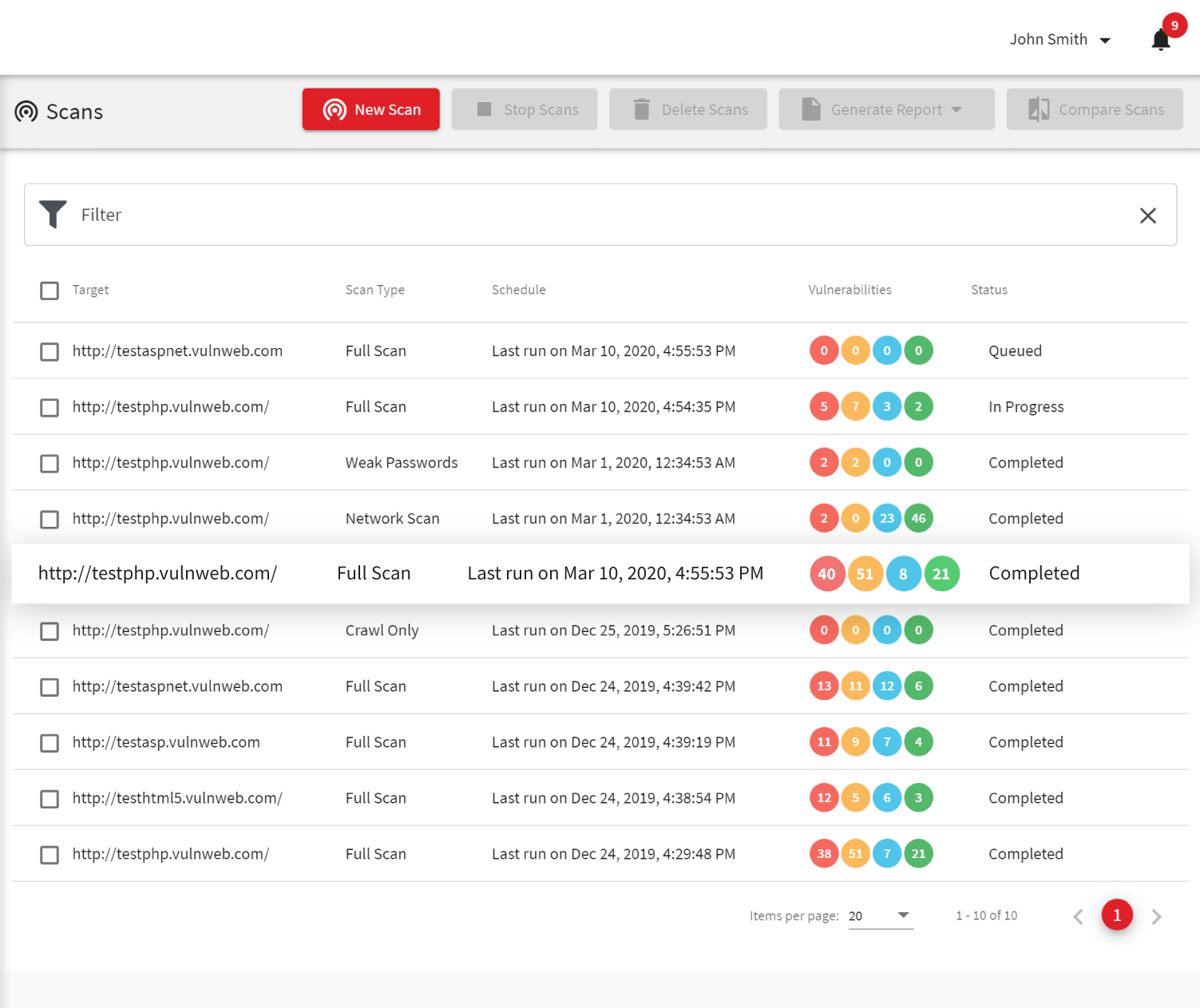
A Web Vulnerability Scanner to Secure All Your Websites and Web Applications
Acunetix is built to detect website security issues in any websites and web applications, independent whether they are built by your teams or based on open-source and commercial products. The online version of Acunetix can scan any web resource and web API as long as you can make it accessible using a public IP address.
- Acunetix features a lot of specific vulnerability tests for popular web products including CMS systems such as WordPress, Joomla, Drupal, and more. It’s vulnerability scan also finds vulnerabilities in plugins, which are often the cause of major security holes, especially in the case of WordPress security.
- Because Acunetix uses a black-box scanning technology (DAST), you can scan all your applications independent of the technologies used to develop them (for example, PHP, Java, and more). Acunetix can also scan web applications based on complex JavaScript, HTML5, and Ajax.
- The Acunetix 360 enterprise solution additionally features a unique crawling engine that detects your web assets. The engine’s active scan continuously scans the Internet searching for public assets that may belong to your company and uses information from domain registrars and SSL certificates.
Frequently asked questions
Web vulnerabilities can be very dangerous and let criminals steal your sensitive information. Attackers can also use such vulnerabilities to impersonate your users or conduct successful phishing campaigns undermining your reputation. No matter whether you create your own web assets or use ready-made software, you should check them for web vulnerabilities.
To find out how many websites have web vulnerabilities, read our yearly report.
Both types of vulnerability scanners are just as good. You have to choose one depending on your particular needs. For example, you need less time to configure an online vulnerability scanner but you can more easily scan web applications on the intranet using an on-premise (local) solution.
The two Acunetix products that are available online are Acunetix Premium and Acunetix 360. Acunetix Premium is designed for mid-size organizations, while Acunetix 360 is a full vulnerability assessment and vulnerability management solution for enterprises with outstanding integration capabilities.
No, Acunetix Online and Acunetix On-Premise are treated as separate licenses. They have the same functionality and the same codebase but you cannot switch between one an the other at will. If you need both on-premise and online scanning, contact us to discuss how we can help you achieve that.

We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.